Microsoft’s Active Directory (AD), introduced in 2000, has been a cornerstone of enterprise identity management. Over the years, it has powered the organization of resources such as computers, printers, and users in a domain/tree/forest structure, typically using Domain Controllers (DCs) for authentication and management. But as businesses moved to the cloud, the need for a solution that integrates both on-premises and cloud environments led to the creation of Azure Active Directory (Azure AD). In this blog post, we’ll dive into the key differences between AD and Azure AD, and how Azure AD Connect plays a crucial role in bridging these two.
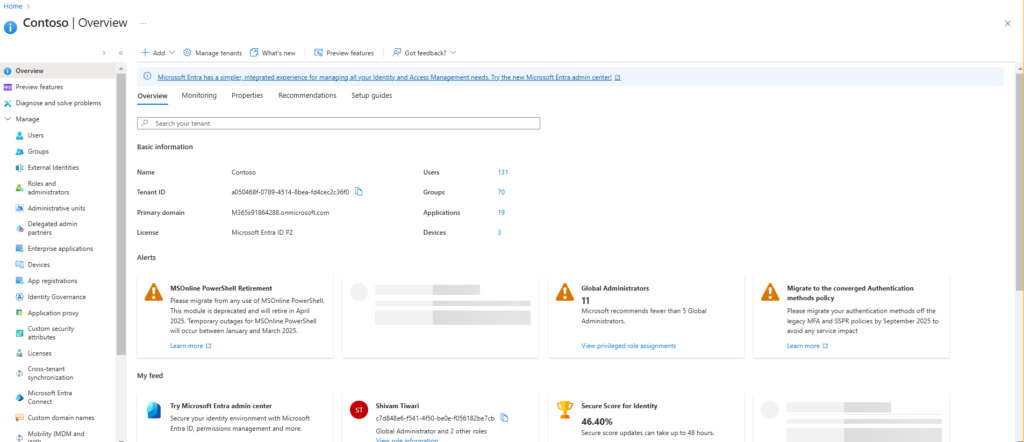
The most fundamental difference between Active Directory and Azure AD is their architecture. While traditional AD has been widely used for on-premises setups, Azure AD was designed specifically for cloud environments. Let’s compare the two to understand Azure AD better:
Communication Protocols:
- AD uses LDAP (Lightweight Directory Access Protocol) for communication, whereas Azure AD leverages REST APIs for interactions. The shift to REST APIs in Azure AD is essential for cloud-based operations, allowing cloud services to be easily invoked via API calls.
Authentication:
- Traditional AD relies on protocols like Kerberos and NTLM for authentication, while Azure AD utilizes cloud-based authentication protocols for its cloud-first approach.
Access Setup:
- AD organizes users using Admin/Data Owners, and employs a hierarchical structure with Forest/Domain/Tree/Organizational Units (OU). Azure AD, on the other hand, organizes users into groups to manage access across cloud resources.
Network Organization:
- In AD, resources are organized into domains and trees, and a forest structure manages multiple domains. Azure AD simplifies this with users and groups.
Desktops and Device Management:
- AD uses Group Policy Objects (GPO) to manage desktops, while Azure AD leverages Microsoft Intune to join desktops to the cloud.

In many enterprise environments, there’s a need to maintain both on-premises AD and Azure AD for seamless operations across hybrid IT setups. This is where Azure AD Connect comes in. Azure AD Connect synchronizes user accounts and passwords between the on-premises Active Directory and Azure AD to ensure users have consistent access to both on-premises and cloud resources.
There are several methods of synchronization with Azure AD Connect:
- Hash Synchronization: In this method, only a hashed version of the password is stored in Azure AD, ensuring secure access without compromising sensitive information.
- Pass-through Authentication (PTA): PTA forwards authentication requests to the on-premises AD server, ensuring that user credentials are always validated locally.
- Federation: Federation services enable authentication across multiple external identities, extending access control to other resources and cloud services.
Azure AD comes with several features that simplify enterprise identity management in the cloud. Let’s look at some of these features:
Default Domain and Custom Domains: When you create an Azure AD tenant, your default domain will be based on your email ID with a
.onmicrosoft.comsuffix. If you’d like to use your company’s domain name, you can add custom domain names to Azure AD for a more personalized experience.App Registrations: Azure AD allows you to register your applications and assign access to users, ensuring that only authorized users can access specific apps.
License Management: With Azure AD, you can track licenses to avoid overuse and manage the assigned licenses across your organization to prevent unnecessary expenses.
Enterprise Applications: You can manage all your enterprise applications in one place and control user access. Users will only see the applications that are assigned to them, simplifying management.
Security is a top priority for Azure AD, and Microsoft provides a suite of tools to help ensure the safety of your cloud resources. Here are some key security features:
Azure AD Conditional Access: This feature allows you to enforce conditional access policies, such as restricting access from specific locations or IP ranges. You can, for instance, prevent users from logging in outside your office network or even outside your country.
Azure AD Identity Protection: This feature assesses risk in real time, evaluating factors like unusual geography of logins or other suspicious activities, and taking automatic actions to mitigate potential threats.
Identity Secure Score: Azure AD provides an identity secure score that tells you how secure your environment is based on your configuration and activities. This score helps identify areas for improvement.
Named Locations: For enhanced conditional access, you can create named locations based on trusted regions (e.g., headquarters or branch offices) and allow access only from these regions.
Multi-Factor Authentication (MFA): Azure AD allows you to enable MFA to add an additional layer of security. This ensures that even if credentials are compromised, attackers cannot easily access your resources.
Authentication Methods: Azure AD supports multiple authentication methods like FIDO2 Security Key and Microsoft Authenticator, enhancing flexibility and security.
Conclusion
Azure Active Directory is a powerful tool for managing identity and access in a cloud-first world. While traditional Active Directory served its purpose for on-premises setups, Azure AD offers robust, scalable, and secure identity management for cloud applications and hybrid environments. With features like Azure AD Connect, conditional access policies, and multi-factor authentication, Azure AD is an essential part of any modern enterprise IT strategy.
By leveraging Azure AD’s capabilities, organizations can ensure secure access, streamline identity management, and embrace the cloud with confidence.
Azure Active Directory, Active Directory, Azure AD, enterprise identity management, Azure AD Connect, hybrid environment, Azure AD security, conditional access, MFA, group policy, Microsoft Intune, app registrations, cloud-based authentication, password synchronization, federation, custom domain name, license management, enterprise applications, REST API, Kerberos, NTLM.












Leave a Reply