Objective
This tutorial outlines the steps required to provision worker data from Workday into Microsoft Entra ID.
Note:
Use this tutorial if the users you want to provision from Workday are cloud-only users who do not require an on-premises AD account. If users require an on-premises AD account or both an AD and a Microsoft Entra account, please refer to the tutorial on configuring Workday for Active Directory user provisioning.
Overview
The Microsoft Entra user provisioning service integrates with the Workday Human Resources API to provision user accounts. The supported Workday user provisioning workflows enable automation of various human resources and identity lifecycle management scenarios, including:
1. Hiring New Employees
When a new employee is added to Workday, a user account is automatically created in Microsoft Entra ID. Optionally, accounts can also be created in Microsoft 365 and other SaaS applications supported by Microsoft Entra ID. Additionally, the email address can be written back to Workday.
2. Employee Attribute and Profile Updates
When an employee’s record in Workday is updated (e.g., changes to their name, title, or manager), the corresponding user account is automatically updated in Microsoft Entra ID. Optionally, these updates can also apply to Microsoft 365 and other supported SaaS applications.
3. Employee Terminations
When an employee is terminated in Workday, their user account is automatically disabled in Microsoft Entra ID. Optionally, the termination can extend to Microsoft 365 and other supported SaaS applications.
4. Employee Rehires
When an employee is rehired in Workday, their previous account can either be reactivated or reprovisioned (based on your preference) in Microsoft Entra ID. Optionally, this process can also apply to Microsoft 365 and other supported SaaS applications.
Who Is This User Provisioning Solution Best Suited For?
The Workday-to-Microsoft Entra user provisioning solution is ideally suited for:
Organizations Seeking a Pre-Built, Cloud-Based Solution
Businesses looking for a ready-to-use, cloud-based solution to handle Workday user provisioning.Organizations Requiring Direct User Provisioning
Companies that need seamless user provisioning directly from Workday to Microsoft Entra ID.Organizations That Depend on Workday Data
Organizations that require user accounts to be provisioned using data sourced directly from Workday.Organizations Using Microsoft 365 for Email
Businesses utilizing Microsoft 365 as their primary email platform.
Architecture
The end-to-end user provisioning solution for cloud-only users consists of two primary flows:
1. Authoritative HR Data Flow (Workday to Microsoft Entra ID)
This flow manages worker events originating in Workday (e.g., New Hires, Transfers, Terminations) and directs them into Microsoft Entra ID. Depending on the nature of the event, corresponding actions are performed in Microsoft Entra ID, such as:
- Creating new user accounts
- Updating existing user profiles
- Enabling or disabling accounts
2. Writeback Flow (On-Premises Active Directory to Workday)
After account creation in Active Directory, the account details are synced with Microsoft Entra ID through Microsoft Entra Connect. Key information such as email, username, and phone number can then be written back to Workday.
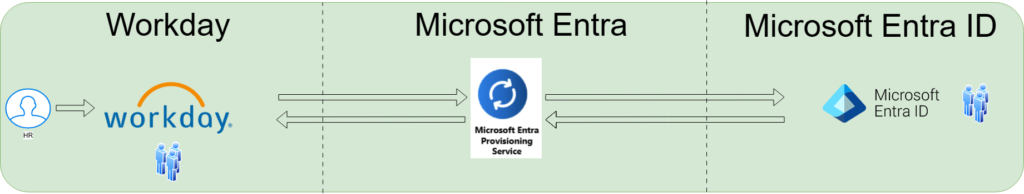
End-to-End User Data Flow
HR Transactions in Workday
The HR team performs worker transactions such as Joiners, Movers, and Leavers (New Hires, Transfers, Terminations) in Workday Employee Central (Workday EC).Scheduled Synchronizations
The Microsoft Entra provisioning service runs scheduled identity synchronizations from Workday EC. It identifies changes that need to be processed and synced with on-premises Active Directory.Processing Changes
Based on the identified changes, the Microsoft Entra provisioning service performs the necessary operation in Microsoft Entra ID, such as:- Creating a new user
- Updating existing user details
- Enabling or disabling a user account
Attribute Retrieval (if Workday Writeback is Configured)
If the Workday Writeback app is enabled, it retrieves key attributes—such as email, username, and phone number—from Microsoft Entra ID.Updating Workday
The Microsoft Entra provisioning service writes back these attributes (email, username, and phone number) into Workday.
Planning Your Deployment
Deploying cloud HR-driven user provisioning from Workday to Microsoft Entra ID requires thorough planning across several key aspects:
-
Determining the Matching ID
- Identify the attribute that will serve as the unique identifier for matching users between Workday and Microsoft Entra ID.
- Ensure consistency in this attribute across both systems to avoid duplicate or mismatched accounts.
-
Attribute Mapping
- Map attributes from Workday to their corresponding attributes in Microsoft Entra ID.
- Define the required fields, such as name, title, email, manager, and others, to ensure accurate user data synchronization.
-
Attribute Transformation
- Plan for any transformations needed to align data formats or conventions between systems.
- For example, splitting or combining fields, normalizing naming conventions, or formatting phone numbers.
-
Scoping Filters
- Define filters to control which users are provisioned from Workday to Microsoft Entra ID.
- Scoping criteria might include location, department, employment status, or other custom attributes.
Configure User Provisioning from Workday to Microsoft Entra ID
The following steps guide you through configuring user provisioning for cloud-only deployments:
1. Add the Microsoft Entra Provisioning Connector App and Connect to Workday
- Add the Microsoft Entra provisioning connector app to your Microsoft Entra ID tenant.
- Set up the connection between Microsoft Entra ID and Workday by providing necessary credentials and configuring API access.
2. Configure Workday and Microsoft Entra Attribute Mappings
- Define and map attributes from Workday (e.g.,
First Name,Last Name,Email) to their corresponding fields in Microsoft Entra ID. - Apply any required attribute transformations to ensure data consistency.
3. Enable and Launch User Provisioning
- Enable the provisioning service in Microsoft Entra ID.
- Run an initial synchronization to validate the configuration and ensure proper data flow.
- Monitor provisioning logs to verify successful creation, updates, or disabling of accounts.
Part 1: Adding the Microsoft Entra Provisioning Connector App and Creating the Connection to Workday
Follow these steps to configure Workday-to-Microsoft Entra provisioning for cloud-only users:
1. Sign In to the Microsoft Entra Admin Center
- Log in with at least Cloud Application Administrator privileges.
2. Add the Workday Provisioning Connector App
- Navigate to Identity > Applications > Enterprise Applications > New Application.
- Search for Workday to Microsoft Entra User Provisioning in the gallery.
- Select and add the app to your tenant.
3. Access the App’s Provisioning Settings
- Once the app is added, go to the app details screen.
- Select Provisioning from the left-hand menu.
- Change the Provisioning Mode to Automatic.
4. Configure Admin Credentials
Complete the following fields in the Admin Credentials section:
- Workday Username: Enter the username for the Workday integration system account, followed by the tenant domain name. For example:
username@contoso4 - Workday Password: Provide the password for the Workday integration system account.
- Workday Web Services API URL: Enter the URL to the Workday web services endpoint for your tenant. This determines the API version used by the connector.
5. Workday Web Services API URL Format
| URL Format | WWS API Version Used | XPATH Changes Required |
|---|---|---|
https://####.workday.com/ccx/service/tenantName |
v21.1 | No |
https://####.workday.com/ccx/service/tenantName/Human_Resources |
v21.1 | No |
https://####.workday.com/ccx/service/tenantName/Human_Resources/v##.# |
v##.# | Yes |
Important Notes
-
Default WWS API Version
- If the URL does not specify a version, the connector uses Workday Web Services (WWS) v21.1 by default.
- No changes are required to the default XPATH API expressions included with the app.
-
Specifying a WWS API Version
- To use a specific WWS API version, include the version number in the URL.
- Example:
https://wd3-impl-services1.workday.com/ccx/service/contoso4/Human_Resources/v34.0
-
Using WWS API v30.0+
- For WWS API versions v30.0 and above, update the XPATH API expressions before enabling the provisioning job:
- Navigate to Attribute Mapping > Advanced Options > Edit Attribute List for Workday.
- Refer to the Managing Your Configuration and Workday Attribute Reference section for guidance on necessary updates.
- For WWS API versions v30.0 and above, update the XPATH API expressions before enabling the provisioning job:
Completing the Configuration
-
Notification Email
- Enter your email address in the Notification Email field.
- Check the box to “Send email if failure occurs” for proactive monitoring.
-
Test the Connection
- Click the Test Connection button to verify the connection.
-
Save the Configuration
- If the connection test succeeds, click the Save button at the top.
- If the test fails, review and confirm the Workday URL and credentials are correct.
Part 2: Configure Workday and Microsoft Entra Attribute Mappings
In this section, you’ll configure how user data flows from Workday to Microsoft Entra ID for cloud-only users.
1. Configure Source Object Scope
- On the Provisioning tab under Mappings, select Synchronize Workers to Microsoft Entra ID.
- In the Source Object Scope field, define which sets of users in Workday should be provisioned to Microsoft Entra ID using attribute-based filters.
Examples of Attribute-Based Filters
-
Filter: Scope to users with Worker IDs between 1000000 and 2000000
- Attribute:
WorkerID - Operator:
REGEX Match - Value:
(1[0-9][0-9][0-9][0-9][0-9][0-9])
- Attribute:
-
Filter: Only contingent workers, not regular employees
- Attribute:
ContingentID - Operator:
IS NOT NULL
- Attribute:
2. Configure Target Object Actions
- Use the Target Object Actions field to globally filter actions performed on Microsoft Entra ID.
- Commonly selected actions:
- Create
- Update
3. Configure Attribute Mappings
- In the Attribute Mappings section, define how individual attributes flow from Workday to Microsoft Entra ID.
- To modify an existing mapping, click on it.
- To add a new mapping, select Add New Mapping at the bottom of the screen.
Attribute Mapping Properties
-
Mapping Type
- Direct: Writes the value of the Workday attribute to the target attribute without modifications.
- Constant: Writes a static, constant string to the target attribute.
- Expression: Creates a custom value for the target attribute using one or more Workday attributes.
-
Source Attribute
- Specifies the Workday attribute to sync.
- If an attribute is missing, refer to the Customizing the List of Workday User Attributes section.
-
Default Value (Optional)
- Specifies a fallback value if the source attribute is empty.
- Typically left blank.
-
Target Attribute
- Specifies the Microsoft Entra ID attribute to sync with the source.
-
Match Objects Using This Attribute
- Indicates if the attribute uniquely identifies users between Workday and Microsoft Entra ID.
- Commonly, the Worker ID in Workday is mapped to the Employee ID attribute or an extension attribute in Microsoft Entra ID.
-
Matching Precedence
- When multiple matching attributes are configured, they’re evaluated in the defined order.
- Matching stops once a match is found.
-
Apply This Mapping
- Always: Applies the mapping for both user creation and updates.
- Only During Creation: Applies the mapping only during user creation actions.
4. Save Your Configuration
- Once your mappings are complete, click Save at the top of the Attribute-Mapping section.
Enable and Launch User Provisioning
Once the Workday provisioning app configurations are completed, you can enable the provisioning service.
1. Turn On the Provisioning Service
- In the Provisioning tab, set the Provisioning Status to On.
- Click Save to initiate the provisioning service.
2. Initial Synchronization
- The operation begins the initial sync, which may take several hours depending on the number of users in the Workday tenant.
- You can track the progress of the sync cycle using the progress bar.
3. Monitor the Provisioning Logs
- At any time, check the Provisioning tab in the Microsoft Entra admin center to see the actions performed by the provisioning service.
- The Provisioning logs will display individual sync events, such as:
- Users being read from Workday
- Users being added or updated in Microsoft Entra ID
4. Audit Summary Report
- Once the initial sync is complete, an audit summary report will be generated and displayed in the Provisioning tab.
Best Practices
-
Source Object Scope Filter:
By default, enabling the provisioning service will initiate operations for all users in scope.
To avoid errors caused by mapping or Workday data issues, it’s recommended to:- Configure a Source Object Scope filter to limit the scope initially.
- Test the attribute mappings with a few test users before launching the full sync.
-
Gradual Expansion:
Once you’ve verified that the mappings work as expected, you can either: - Remove the filter.
- Gradually expand the filter to include more users.











Leave a Reply