Azure Kubernetes Service (AKS) Complete Guide: Architecture, Security & Troubleshooting
Azure Kubernetes Service (AKS) is Microsoft Azure’s fully managed Kubernetes platform. It simplifies how you deploy, scale, secure, and operate containerized workloads in the cloud. In this guide from CloudKnowledge, we’ll walk through everything you need to build a production-grade Azure Kubernetes Service (AKS) environment — from architecture and networking to security, DevOps, cost optimization, and real-world troubleshooting with PowerShell and Azure CLI.
1. What Is Azure Kubernetes Service (AKS)?
Azure Kubernetes Service (AKS) is a managed Kubernetes service that offloads the heavy lifting of Kubernetes control-plane management to Azure. Microsoft runs and patches the API server, etcd, and critical control-plane components, while you focus on deploying and managing workloads on the worker nodes.
With Azure Kubernetes Service (AKS) you get:
- Fully managed Kubernetes control plane (no master node VMs to manage).
- Integrated Azure networking, identity, monitoring, and security tools.
- Built-in support for autoscaling, multi-node pools, and availability zones.
- First-class integration with Azure DevOps and GitOps workflows.
Key Points: Azure Kubernetes Service (AKS) Basics
- Azure manages the Kubernetes control plane; you manage worker nodes and workloads.
- AKS uses standard upstream Kubernetes, so skills and manifests are portable.
- Deep integration with Azure services like Azure Monitor, Key Vault, and Microsoft Entra ID.
- Ideal platform for microservices, APIs, event-driven and batch workloads.
Mini FAQs – Getting Started with Azure Kubernetes Service (AKS)
Q1. Is Azure Kubernetes Service (AKS) free?
The AKS control plane is free; you only pay for the cluster’s worker nodes and attached services like storage, load balancers, and monitoring. This makes Azure Kubernetes Service (AKS) cost-effective for both development and production clusters.
Q2. Do I need to learn Kubernetes before using AKS?
Yes, basic Kubernetes concepts (pods, services, deployments, namespaces) are essential. Microsoft provides a free learning path: Intro to Kubernetes on Azure .
Q3. Can I run both Linux and Windows containers on Azure Kubernetes Service (AKS)?
Yes. You can use multiple node pools with different OS types (Linux and Windows) in a single cluster and schedule workloads accordingly.
2. Why Enterprises Choose Azure Kubernetes Service (AKS)
When organizations modernize monoliths into microservices, they need a platform that offers elasticity, security, and operational consistency. Azure Kubernetes Service (AKS) answers this with:
- Fully managed Kubernetes control plane with automated upgrades and patches.
- Deep Azure ecosystem integration for monitoring, policies, secret management, and DevOps.
- Enterprise-grade security posture with Microsoft Entra ID RBAC, network policies, and private clusters.
- Flexible node management via VM scale sets, GPU pools, spot nodes, and autoscaling.
- Multi-region, multi-cluster support using Azure Front Door, Traffic Manager, and Azure Arc.
For a reference production baseline, see the official Baseline architecture for an Azure Kubernetes Service (AKS) cluster .
Key Points: Strong, Rank-Friendly AKS Benefits
- Azure Kubernetes Service (AKS) removes control-plane toil, letting teams focus on apps.
- Built-in scaling (cluster autoscaler, HPA, KEDA) handles elastic workloads efficiently.
- Azure Policy and Defender for Cloud bring governance and security into the CI/CD loop.
- Serverless add-ons and spot nodes significantly lower cost for bursty workloads.
Mini FAQs – Why Azure Kubernetes Service (AKS)?
Q1. How is AKS different from running Kubernetes on virtual machines?
In a self-managed Kubernetes cluster you own everything: control plane, etcd, upgrades, backup, etc. With Azure Kubernetes Service (AKS) the control plane is fully managed and backed by an SLA, reducing operational overhead and risk.
Q2. Does AKS support GitOps?
Yes. AKS integrates with Flux v2 and Azure Arc for GitOps-based deployments. You can declaratively sync cluster state from Git repositories, improving reliability and auditability.
3. Azure Kubernetes Service (AKS) Architecture Explained
A well-designed Azure Kubernetes Service (AKS) cluster separates concerns across control plane, worker nodes, networking, and external dependencies. The official baseline architecture provides a battle-tested pattern.
3.1 Control Plane (Managed by Azure)
The control plane includes the Kubernetes API server, scheduler, controller manager, and etcd. Azure runs these components in a separate, managed resource group. You don’t manage these VMs directly; instead you interact through the Kubernetes API and Azure APIs.
3.2 Node Pools & VM Scale Sets
AKS uses Azure Virtual Machine Scale Sets (VMSS) to manage worker nodes. Common patterns:
- System node pool: runs critical system pods like CoreDNS and metrics-server.
- User node pools: run business workloads; you can create multiple pools per workload type.
- Specialized pools: GPU-enabled pools, spot node pools, or pools tuned for memory/CPU.
3.3 Networking & Azure CNI
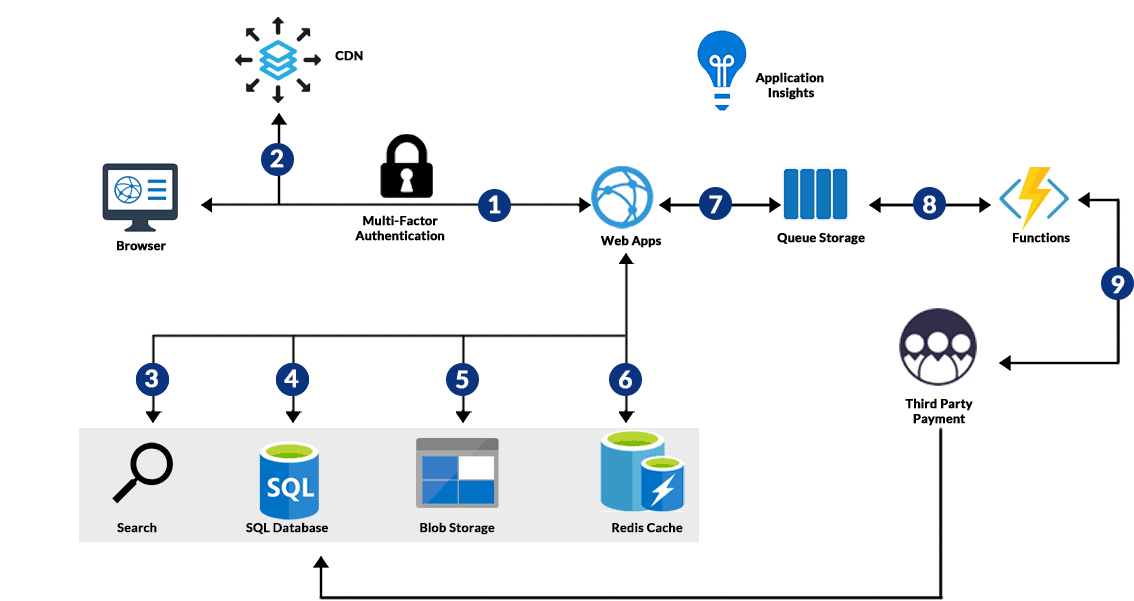
For production clusters, Microsoft recommends Azure CNI or Azure CNI Powered by Cilium. Each pod gets an IP address from the virtual network subnet, enabling fine-grained network policies and seamless integration with Azure Firewall, Azure Application Gateway, and on-prem networks.
3.4 Ingress, Load Balancers & External Dependencies
A typical Azure Kubernetes Service (AKS) deployment uses:
- Azure Load Balancer or Application Gateway for north-south traffic.
- Ingress controllers (NGINX, AGIC, Application Gateway for Containers) for HTTP routing.
- External data stores such as Azure Cosmos DB, Azure SQL, or Azure Cache for Redis.
- Azure Service Bus, Event Hubs, or Storage Queues for asynchronous messaging.
Key Points: AKS Architecture
- Separate system and user node pools for better isolation and scalability.
- Use Azure CNI for production-grade, policy-driven networking.
- Keep state (databases, queues) in managed services outside the cluster.
- Integrate with Azure Key Vault for secrets via the Secrets Store CSI driver.
Mini FAQs – AKS Architecture
Q1. Should I run databases inside Azure Kubernetes Service (AKS)?
For most workloads, the best practice is to use managed services like Azure SQL, Azure Cosmos DB, or Azure Database for PostgreSQL instead of running databases inside AKS. This improves reliability and simplifies backup and scaling.
Q2. How many node pools should I use?
At minimum, use one system node pool and one user node pool. Add more user node pools for isolation (for example, front-end, background jobs, GPU workloads, or environment-specific pools).
4. Microservices on Azure Kubernetes Service (AKS)
Azure Kubernetes Service (AKS) is a natural fit for microservices. You can package each microservice in its own container, deploy them as Kubernetes deployments, and expose them via services and ingress routes.
4.1 Typical Microservices Flow
- Client requests enter via Azure Front Door or Application Gateway.
- Traffic is forwarded to an ingress controller in the Azure Kubernetes Service (AKS) cluster.
- Ingress routes requests to the appropriate front-end or API microservice.
- Microservices communicate internally via ClusterIP services or service mesh (Istio, Linkerd).
- State is stored in Azure-managed services (Cosmos DB, SQL, Redis) outside the cluster.
The official reference architecture is documented in Advanced Azure Kubernetes Service (AKS) microservices architecture .
Key Points: Microservices on Azure Kubernetes Service (AKS)
- Use separate namespaces per application or domain boundary for better tenancy and RBAC.
- Adopt a service mesh for traffic control, mTLS, and distributed tracing across microservices.
- Use health probes and pod disruption budgets for resilient rolling upgrades.
- Deploy each microservice independently using GitOps or CI/CD pipelines.
Mini FAQs – AKS Microservices
Q1. Do I need a service mesh for every AKS microservices deployment?
No. Start without a service mesh if your architecture is simple. Introduce a mesh when you need features like traffic shadowing, canary releases, or detailed per-request telemetry.
Q2. How do I implement zero-downtime deployments?
Use rolling updates with readiness and liveness probes, and consider blue/green or canary strategies via ingress routing or a service mesh. Azure DevOps and GitHub Actions both support these patterns.
5. Security, Identity & Governance in Azure Kubernetes Service (AKS)
Enterprise-grade security is a core reason to adopt Azure Kubernetes Service (AKS). Secure clusters combine Microsoft Entra ID, managed identities, Key Vault, network controls, and policies.
5.1 Microsoft Entra ID Integration & RBAC
- Integrate AKS with Microsoft Entra ID for user and group-based cluster RBAC.
- Map Entra groups (for example,
aks-admins,aks-devs) to Kubernetes roles. - Use Azure RBAC for AKS to control who can create, scale, or delete clusters.
5.2 Managed Identities & Key Vault
- Use managed identities for cluster and workloads to access Azure resources without secrets.
- Use Azure Key Vault plus the Secrets Store CSI driver to mount secrets as volumes in pods.
- Rotate secrets and certificates regularly and avoid plain-text secrets in Kubernetes manifests.
5.3 Network Security & Policies
- Enable Azure CNI network policies or Cilium for in-cluster micro-segmentation.
- Use Azure Firewall or a third-party firewall for inspecting outbound and inbound traffic.
- Use private clusters and disable public access where possible.
5.4 Policy & Compliance
Azure Policy for Kubernetes lets you audit and enforce configuration standards:
- Block privileged containers.
- Enforce allowed registry images (for example, only from Azure Container Registry).
- Require resource limits and liveness/readiness probes.
Key Points: Securing Azure Kubernetes Service (AKS)
- Use Microsoft Entra ID groups and Kubernetes RBAC instead of individual user bindings.
- Prefer managed identities over service principals for long-term security.
- Combine network policies, private clusters, and Azure Firewall for defense-in-depth.
- Use Azure Policy to prevent insecure configurations from ever being deployed.
Mini FAQs – AKS Security
Q1. How do I secure kubectl access?
Use Microsoft Entra ID integration and short-lived tokens, limit admin access, and log all
API server actions with Azure Monitor and Azure Activity Logs. Use --admin credentials only
for break-glass scenarios.
Q2. Can I restrict which container registry AKS pulls from?
Yes. Use Azure Policy to restrict allowed container registries and enable Azure Defender for Containers for image scanning and runtime protection.
6. Networking, Ingress, WAF & Hub-Spoke Design
Most production Azure Kubernetes Service (AKS) deployments use a hub-spoke network topology: the hub hosts shared services (for example, Azure Firewall), while each spoke hosts application VNets including AKS.
6.1 Typical Flow
- Public internet traffic terminates on Azure Front Door or Application Gateway with Web Application Firewall (WAF).
- Traffic travels through hub-spoke VNet peering to the AKS subnet.
- Inside the spoke, an internal load balancer forwards traffic to the ingress controller in AKS.
- Azure Firewall controls egress from the AKS subnet to the internet or on-prem networks.
Learn more in the secure baseline architecture for AKS .
Key Points: AKS Networking Patterns
- Use hub-spoke to centralize security appliances and logging.
- Expose AKS through Application Gateway or Front Door with WAF.
- Use private endpoints for databases and other PaaS services.
- Leverage NAT Gateway or UDR + Firewall for controlled outbound access.
Mini FAQs – AKS Networking
Q1. Should I use public or private clusters?
For production, prefer private clusters where the API server is accessible only from your VNets. Public clusters are simpler but expand the attack surface.
Q2. How do I secure outbound traffic from AKS?
Use Azure Firewall or NAT Gateway with user-defined routes (UDR). Lock down allowed destinations via FQDN tags, IP groups, or network rules.
7. CI/CD & GitOps for Azure Kubernetes Service (AKS)
Modern AKS deployments rely on pipelines instead of manual kubectl commands. The recommended pattern is to combine CI pipelines (build, test, image push) with GitOps-based CD.
7.1 CI Pipeline (Build & Test)
- Use Azure Pipelines or GitHub Actions to build container images.
- Scan images for vulnerabilities and push them to Azure Container Registry (ACR).
- Tag images with semantic versions and commit IDs.
7.2 CD Pipeline (GitOps)
- Store Kubernetes manifests or Helm charts in a Git repository.
- Use Flux or Argo CD to sync the cluster state from Git.
- Use environment branches or folders (dev, test, prod) to separate configurations.
See the official guidance on GitOps with Azure Kubernetes Service (AKS) .
Key Points: DevOps with Azure Kubernetes Service (AKS)
- Automate image builds and security scans for every commit.
- Use Git as the single source of truth for cluster configuration.
- Promote releases across environments using pull requests, not manual commands.
- Integrate policy checks and quality gates in CI/CD pipelines.
Mini FAQs – AKS CI/CD
Q1. Which is better for AKS: Helm or Kustomize?
Both work well. Helm is template-driven and popular for packaged charts; Kustomize is patch-based and built into kubectl. Many teams mix both depending on workload needs.
Q2. Can I deploy directly from Azure DevOps without GitOps?
Yes, you can, but GitOps provides stronger auditability and rollback safety. Consider starting with classic pipelines and gradually evolve to GitOps.
8. Node Pools, Scaling & Cost Optimization in Azure Kubernetes Service (AKS)
Cost optimization on Azure Kubernetes Service (AKS) revolves around right-sizing node pools, using autoscaling, and shutting down unused clusters or node pools.
8.1 Node Pools & Autoscaling
- Use cluster autoscaler to add or remove nodes automatically.
- Use Horizontal Pod Autoscaler (HPA) for request/CPU-based scaling of deployments.
- Use KEDA for event-based autoscaling (for example, queue length or custom metrics).
8.2 Spot Nodes & Serverless Options
- Use spot node pools for non-critical, interruptible workloads.
- Consider serverless options like Azure Container Apps for spiky workloads when full AKS is not required.
8.3 Shut Down Clusters Outside Business Hours
For dev/test clusters, schedule automatic stop/start actions using Azure Automation or Functions. This can cut costs significantly.
Key Points: AKS Cost Management
- Right-size node pools and use autoscaling instead of static overprovisioning.
- Use spot VMs for batch processing and non-critical jobs.
- Stop dev/test clusters outside office hours to reduce compute usage.
- Use Azure Cost Management and Azure Advisor recommendations for continuous optimization.
Mini FAQs – AKS Cost
Q1. Does autoscaling increase costs?
Autoscaling can both increase and decrease costs depending on workload. Proper configuration ensures you only pay for the resources you actually need over time.
Q2. How do I estimate AKS cost before deploying?
Use the Azure Pricing Calculator to estimate compute, storage, and networking costs based on node sizes and expected usage.
9. Monitoring & Observability for Azure Kubernetes Service (AKS)
Observability is crucial to successfully run applications on Azure Kubernetes Service (AKS). Azure integrates natively with Log Analytics, Azure Monitor, and Application Insights.
9.1 Core Observability Components
- Container insights for node and pod metrics.
- Log Analytics workspace for storing cluster logs and metrics.
- Application Insights for application-level telemetry and distributed tracing.
- Azure Monitor Alerts for proactive notifications and incident workflows.
9.2 Recommended Dashboards & Alerts
- Cluster and node CPU/memory utilization.
- Pod restart count and crash loops.
- Ingress latency and error rates (4xx, 5xx).
- Autoscaler events and failed scaling attempts.
Key Points: Monitoring Azure Kubernetes Service (AKS)
- Enable Container insights and Application Insights from day one.
- Centralize logs in a single Log Analytics workspace per environment.
- Use Kusto Query Language (KQL) to create custom dashboards and alerts.
- Correlate Kubernetes events with application logs for faster troubleshooting.
Mini FAQs – AKS Observability
Q1. Can I use Prometheus and Grafana with AKS?
Yes. You can deploy them yourself or use the Azure Monitor managed service for Prometheus and Azure Managed Grafana for a managed experience.
Q2. How do I debug a failing pod?
Use kubectl logs for logs, kubectl describe pod for events,
and Container insights for metrics. Check readiness and liveness probes as well as image pull errors.
10. Troubleshooting Azure Kubernetes Service (AKS)
Troubleshooting on Azure Kubernetes Service (AKS) follows a layered approach: start from cluster access, move to nodes, then workloads, then networking and identity. Below are practical steps plus PowerShell and Azure CLI snippets.
10.1 Cluster Access Issues (kubectl Fails)
- Verify you are authenticated to Azure and to the correct subscription.
- Check that
az aks get-credentialsorImport-AzAksCredentialhas been run. - Confirm that your Microsoft Entra ID user or group is assigned the right cluster RBAC role.
10.2 Node & Pod Health Issues
- Check node status and capacity.
- Look for pods in
Pending,Error, orCrashLoopBackOffstate. - Review events and logs for the failing workloads.
10.3 Networking & Ingress Problems
- Verify the Kubernetes service type (LoadBalancer, ClusterIP, NodePort).
- Check if the external IP from the load balancer is provisioned.
- Inspect ingress rules and certificates (for HTTPS).
- Use
kubectl port-forwardto isolate whether the problem is inside AKS or at the edge.
10.4 Identity & RBAC Issues
- Check which Microsoft Entra ID user or group your kubeconfig is using.
- Check Kubernetes RBAC via
kubectl auth can-i. - Confirm cluster-level roles and role bindings.
10.5 Performance & Scaling Issues
- Check node and pod resource utilization.
- Ensure HPA or KEDA is configured correctly.
- Check if the cluster autoscaler has pending scale-up events.
Key Points: AKS Troubleshooting Approach
- Always start from authentication and cluster access.
- Use kubectl
describeandlogsaggressively – they are your best friends. - Use Container insights and KQL queries for pattern detection.
- Script repetitive checks via PowerShell or shell functions.
Mini FAQs – AKS Troubleshooting
Q1. I get “Forbidden” when running kubectl. What should I check?
Verify that your user is in the right Microsoft Entra ID group mapped to a Kubernetes role.
Use kubectl auth can-i to see which actions are allowed.
If you’re cluster admin, ensure you used the --admin flag with
az aks get-credentials only for break-glass scenarios.
Q2. My pods are stuck in Pending state. How can I fix this?
Check node capacity and taints, verify that the requested resources fit available nodes, and confirm that the cluster autoscaler can provision new nodes. Also confirm any node selectors and affinity rules.
11. Useful PowerShell & CLI Scripts for AKS Operations
Below are practical snippets you can adapt when operating Azure Kubernetes Service (AKS). They focus on troubleshooting, inventory, and cost control.
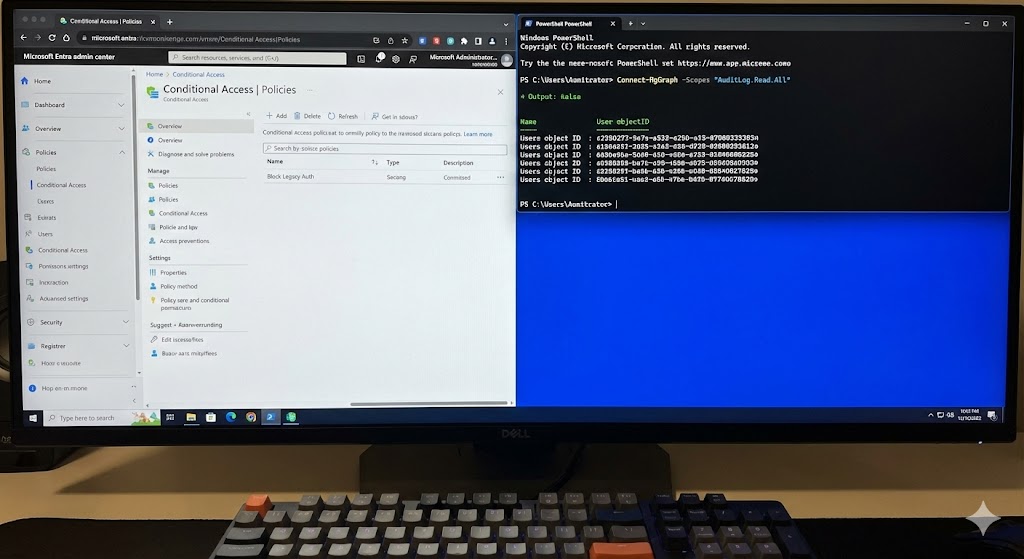
11.1 Connect and Import AKS Credentials (PowerShell)
11.2 Export AKS Cluster Inventory to CSV
Use this script to quickly list clusters, locations, Kubernetes versions, and node counts for auditing or troubleshooting.
11.3 Check Node Pool Details (PowerShell)
11.4 Script to Stop/Start AKS Clusters for Cost Savings
Schedule this script via Azure Automation to stop dev/test clusters at night and start them in the morning.
11.5 Useful Azure CLI One-Liners
Key Points: Scripting AKS Operations
- Use Az.Aks cmdlets for cluster lifecycle, node pools, and upgrade profiles.
- Automate inventory exports for compliance and reporting.
- Use scheduled runbooks to stop/start clusters and save cost.
- Combine PowerShell with KQL queries for advanced troubleshooting.
Mini FAQs – AKS Scripting
Q1. Should I prefer Azure CLI or PowerShell for AKS?
Use whichever fits your workflows. Azure CLI is great for quick commands and pipelines; PowerShell is powerful for scripting and Windows-heavy environments. Many teams use both.
12. Example Microsoft Graph API Scenarios Around AKS RBAC
Azure Kubernetes Service (AKS) is an Azure resource, so its core management happens through Azure Resource Manager, not Microsoft Graph. However, Microsoft Graph is extremely useful when you troubleshoot identity and RBAC around AKS, because it can show which users or groups should have cluster access.
12.1 List Members of an AKS Admin Group with Microsoft Graph
Suppose your AKS cluster uses an Entra ID group called aks-cluster-admins.
If kubectl access fails, verify group membership via Graph.
12.2 Check Application (Service Principal) Credentials Expiry for Legacy AKS Clusters
Older AKS clusters may still use service principals. Expired credentials can break operations. The following Graph call lists credential expirations:
For most new deployments, prefer managed identities instead of service principals to avoid secret rotation issues.
Key Points: Using Microsoft Graph with AKS
- Graph is ideal for inspecting Entra ID users, groups, and app registrations used by AKS.
- Use it to troubleshoot who should have cluster access when RBAC misconfigurations arise.
- Migrate legacy service principal–based clusters to managed identities where possible.
13. Azure Kubernetes Service (AKS) Best-Practices Checklist
Use this checklist as a quick review when designing or auditing an Azure Kubernetes Service (AKS) cluster.
- Use the AKS baseline architecture as a starting point.
- Separate system/user node pools; use at least one user pool per major workload type.
- Use Azure CNI (or Azure CNI powered by Cilium) and network policies for production clusters.
- Integrate Microsoft Entra ID for cluster authentication and Kubernetes RBAC for authorization.
- Store secrets in Azure Key Vault using the Secrets Store CSI driver.
- Enable Container insights, Application Insights, and central logging.
- Adopt GitOps for deployments, with strong CI practices and image scanning.
- Enable Azure Policy for Kubernetes to enforce security and configuration standards.
- Use autoscaling and spot nodes where appropriate to optimize cost.
- Test disaster recovery, backup, and cluster-upgrade processes regularly.
14. Azure Kubernetes Service (AKS) – Global FAQ
Q1. What is the difference between Azure Kubernetes Service (AKS) and Azure Container Apps?
Azure Kubernetes Service (AKS) gives you full control over the Kubernetes platform and is ideal for complex, customizable workloads. Azure Container Apps is a serverless container platform with less control but simpler operations and automatic scaling, based on open-source components like KEDA and Dapr.
Q2. How long does it take to upgrade an AKS cluster?
It depends on node count, workload size, and region. Upgrades are rolling and can be done with minimal downtime when probes and PodDisruptionBudgets are set correctly. Always test upgrades in non-production first.
Q3. Can I run AKS in multiple regions for high availability?
Yes. Use multiple clusters in different regions and front them with Azure Front Door or Traffic Manager. Consider the multi-region guidance from the Azure Architecture Center.
Q4. Where can I learn more about Azure Kubernetes Service (AKS)?
Refer to:
15. Final Thoughts on Azure Kubernetes Service (AKS)
Azure Kubernetes Service (AKS) has become a cornerstone for cloud-native architectures on Azure. By combining a fully managed control plane with deep ecosystem integrations, it allows teams to run microservices, APIs, and data-processing workloads reliably at scale.
For more tutorials, scripts, and real-world troubleshooting guides, visit CloudKnowledge.




Leave a Reply