Learn the difference between Privileged Identity Management (PIM) and Privileged Access Management (PAM), why both matter, how to implement them in cloud-only and hybrid environments, tools, pros/cons, and deep integration examples.
Introduction
Privileged access is the single most valuable (and most-targeted) asset in most organizations. Two related but distinct controls help you secure that surface: Privileged Identity Management (PIM) and Privileged Access Management (PAM). They solve overlapping problems from different angles — PIM focuses on who holds privileged roles and how those roles are governed; PAM focuses on how privileged accounts and credentials are used, secured, and audited. Understanding both, and how to combine them, is key to a strong identity-security posture. Delinea CyberArk
What is PIM?
Privileged Identity Management (PIM) is about governance of privileged identities and roles. It helps you discover who has powerful roles, convert standing (permanent) privileges into eligible (just-in-time) privileges, enforce approval or MFA when privileges are activated, run access reviews, and audit role activations. Microsoft’s Entra (Azure AD) PIM is a canonical example — it lets organizations manage, control, and monitor privileged access to Entra/Azure/Microsoft 365 resources with JIT activation, approvals, and access review capabilities.
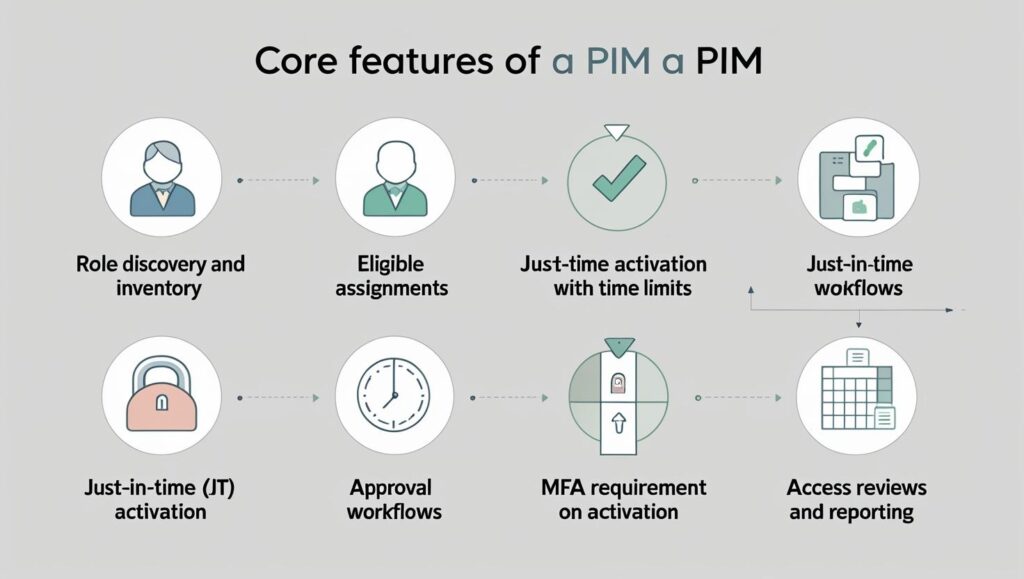
Core PIM features
-
Role discovery and inventory (who has what role)
-
Eligible assignments (make admins eligible rather than permanent)
-
Just-in-time (JIT) activation with time limits
-
Approval workflows, MFA requirement on activation
-
Access reviews and reporting
What is PAM?
Privileged Access Management (PAM) focuses on controlling and protecting privileged accounts and credentials — think service accounts, local admin accounts, cloud root accounts, SSH keys, and stored secrets. PAM solutions vault secrets, rotate credentials automatically, provide session brokering/recording (for RDP/SSH), and enforce check-out/approval workflows and least-privilege elevation for specific tasks. PAM is about the operational control of how privileged credentials are used and audited.
Core PAM features
-
Credential/secret vaulting and automatic rotation
-
Session brokering and recording for remote sessions
-
Privileged session monitoring and real-time controls
-
Just-in-time elevation for local or service accounts (via ephemeral credentials)
-
Audit trails and forensic logs
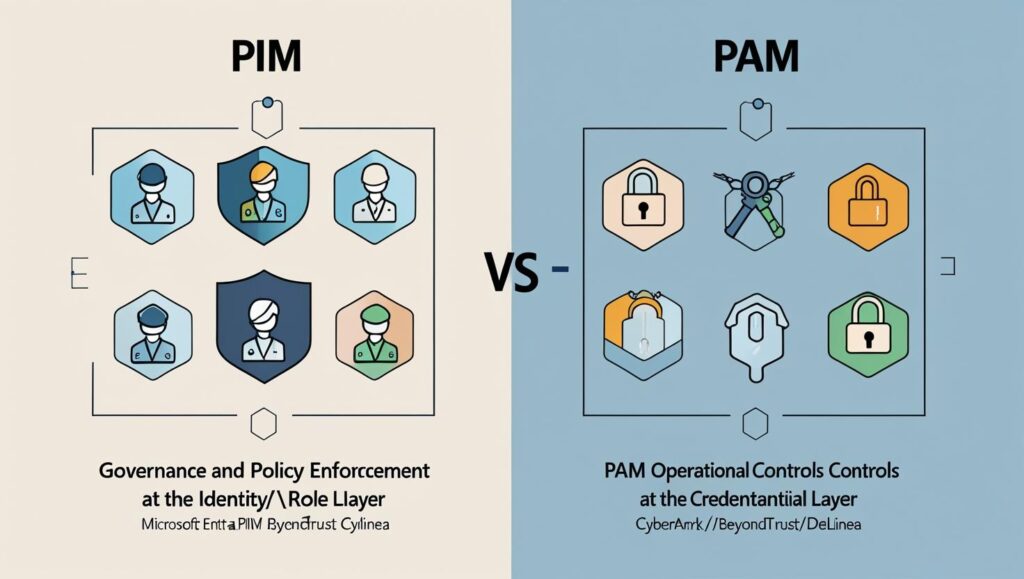
PIM vs PAM — Key differences (short)
- Focus: PIM = who/which roles; PAM = how/which credentials/sessions.
- Artifacts: PIM deals with roles and assignments; PAM deals with accounts, passwords, keys, and sessions.
- Control point: PIM enforces governance/policies at identity/role layer (activation, reviews); PAM enforces operational controls at credential/session layer (vaulting, rotation, recording).
- Typical tools: PIM often part of IAM/IdP (e.g., Microsoft Entra PIM); PAM often provided by specialized vendors (e.g., CyberArk, BeyondTrust, Delinea).
How to use PIM in security (practical)
-
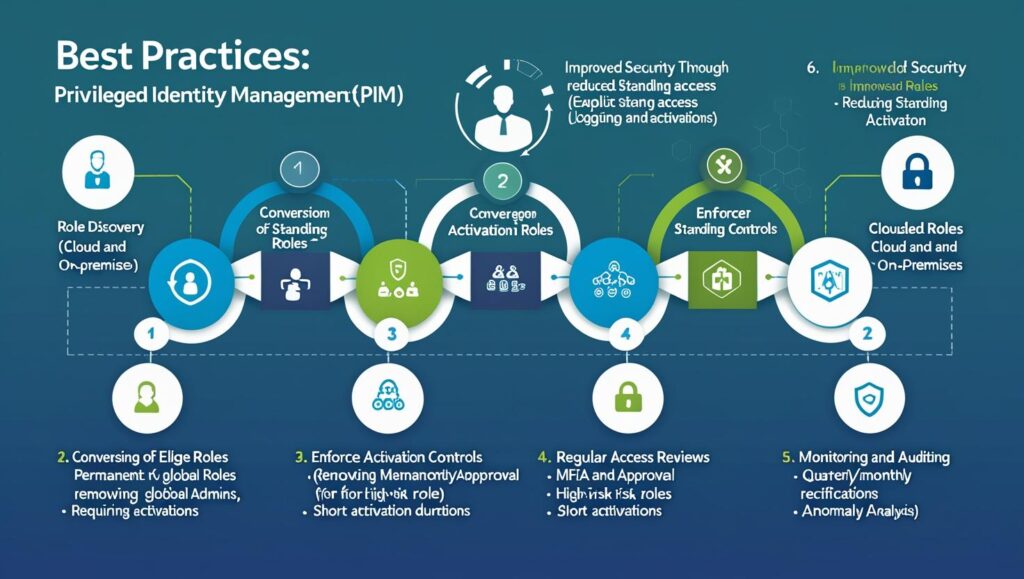
Inventory privileged roles — start with role discovery (cloud and on-prem).
-
Convert standing roles to eligible roles — remove permanent Global Admins; make them eligible and require activation.
-
Enforce activation controls — require MFA and approval for high-risk roles; set short activation durations.
-
Run regular access reviews — recertify privileges quarterly/monthly.
-
Monitor and audit activations — log all activations and analyze for anomalies.
These steps follow proven guidance for Entra/Azure and modern RBAC governance — PIM improves security by reducing standing access and requiring explicit activation for privileged tasks.
What is the use of PAM in security (practical)
PAM reduces credential risk and the attack surface by:
-
Vaulting and rotating credentials so stolen or leaked passwords are short-lived.
-
Controlling remote privileged sessions (users access systems via PAM broker; PAM records and can terminate suspicious sessions).
-
Providing ephemeral credentials for tasks so credentials aren’t persistently stored on endpoints.
-
Delivering detailed audit trails for compliance and forensic investigation.
For cloud environments, PAM handles cloud root/service credentials and for hybrid/on-prem environments it controls domain/local admin accounts — protecting the critical “keys” to systems.
How to integrate PIM — cloud-only and hybrid
Cloud-only (example: Microsoft Entra / Azure)
-
Enable Entra PIM and identify privileged roles (Global Admin, Exchange Admin, etc.).
-
Make admins eligible and define activation policies (MFA, approval, max duration).
-
Add access reviews and alerts for unusual activations; integrate logs with SIEM.
-
Enforce conditional access so privileges only activate from secure locations or compliant devices.
This model is native to cloud identity providers and is straightforward for cloud-native apps and services.
Hybrid (cloud + on-prem)
-
Map on-prem roles to cloud roles and identify break-glass and emergency accounts.
-
Use PIM for cloud components and combine with on-prem controls (e.g., AD tiering).
-
Ensure logging and SIEM aggregation across cloud and on-prem for centralized auditing.
-
Adopt best practices for hybrid privileged access (segmentation, tiered administration, emergency access plans). Implementation patterns and guidance for hybrid deployments are documented in Microsoft best practice and partner resources.
How to integrate PAM — cloud-only and hybrid
Cloud-only
-
Deploy a cloud-hosted/vended PAM (SaaS or cloud-hosted) and onboard cloud accounts (e.g., AWS root, Azure subscription admin, service principals).
-
Vault cloud credentials and enable automatic rotation; require check-out/process before use.
-
Use session brokering for administrative console access and integrate PAM logs with cloud monitoring/SIEM.
Examples exist where PAM vendors help manage AWS root with MFA, vaulting and session control.
Hybrid
-
Install on-prem components/connectors to access domain controllers, Windows/Linux servers, and network devices.
-
Vault and rotate local admin/domain passwords, enforce jump-server access and session recording.
-
Integrate with cloud IdP (e.g., Azure AD) for SSO and conditional access to the PAM portal.
CyberArk and other PAM vendors provide architectures and playbooks for hybrid environments (on-prem + Azure AD integration).
Advantages and Disadvantages
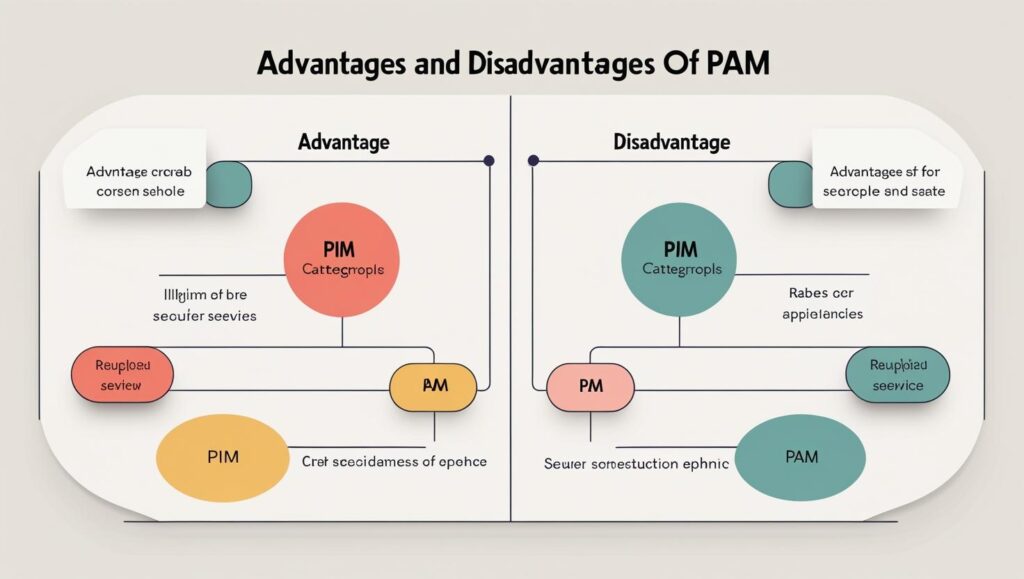
Advantages (PIM)
-
Reduces standing privileged access (good for least-privilege).
-
Native to identity platform (easier cloud integration).
-
Good for role governance and audits.
Disadvantages (PIM)
-
Does not vault or rotate credentials — it governs roles, not secrets.
-
Less effective for non-role based resources (local accounts, service accounts).
Advantages (PAM)
-
Protects credentials and sessions (vaulting, rotation, recording).
-
Strong operational controls for on-prem systems and cloud account secrets.
Disadvantages (PAM)
-
Complexity: PAM deployments and on-boarding can be more operationally heavy.
-
Requires careful integration with IdP for seamless SSO / approval flows.
Applications / Tools used for PIM and PAM
Common PIM tools
-
Microsoft Entra PIM (Azure AD PIM).
-
Identity governance platforms (some features in SailPoint, Saviynt).
Common PAM tools
-
Delinea (formerly Thycotic), BeyondTrust, One Identity, ManageEngine PAM360, HashiCorp Vault (for secrets).
Deep example — PIM integration
Scenario: You want to remove standing Global Admins in a 10,000-user Azure tenant.
Steps:
-
Inventory all accounts with admin roles using Entra report.
-
Plan role owners, map responsibilities and identify emergency (break-glass) accounts (minimize them and secure them offline).
-
Make admins eligible in Entra PIM instead of permanent; configure activation policy: require MFA, require approval for Global Admin, set max activation duration to 1 hour.
-
Enable access reviews monthly for high-risk roles; revoke eligibility if not justified.
-
Integrate logs from Entra PIM with SIEM (e.g., Azure Sentinel / Microsoft Sentinel) to detect suspicious activations or failed activation attempts.
-
Test emergency procedures for break-glass accounts and document the process.
Outcome: Admins only hold elevated privileges when needed (JIT), activations are auditable, and the permanent attack surface from standing privileges is drastically reduced.
Deep example — PAM integration
Scenario: Secure AWS root and privileged EC2 admin access across cloud and on-prem servers using a PAM vendor (example: CyberArk).
Steps:
-
Onboard AWS root and cloud admin accounts into the PAM vault. Configure vault to store credentials and provide API access for rotation.
-
Enable automatic credential rotation for AWS root and privileged IAM users so credentials can’t be reused after compromise.
-
Set up check-out or session launch: users either check out ephemeral credentials after approval or launch a recorded session through the PAM broker.
-
Implement session recording and monitoring for all RDP/SSH/admin console sessions on EC2 and on-prem servers. Recordings are stored in the PAM audit store for review.
-
Integrate PAM with IdP (Azure AD) for SSO to the PAM portal and enforce conditional access before session launch.
-
Automate secrets lifecycle (rotate, retire, re-issue) and feed key events into SIEM for detection.
Outcome: Credentials are no longer long-lived secrets on user machines; sessions are auditable and can be terminated if suspicious behavior is detected.
Conclusion — Which is more secure?
There’s no single answer: PIM and PAM are complementary. PIM reduces the human standing privilege footprint (who has admin roles and when), while PAM protects the credentials and sessions that attackers target. The strongest posture uses both: PIM to minimize standing privileges and require governance/approval, and PAM to vault, rotate and monitor credentials and sessions. Treat them as layered controls — together they make privileged compromise far harder.
Final recommendations
-
Start with role inventory and a PIM plan to remove standing privileges. Microsoft Learn
-
Add a PAM solution to vault and rotate critical credentials and to record privileged sessions. CyberArk
-
Integrate logs from both into your SIEM; run automated access reviews and alert on unusual activations or session behavior.











Leave a Reply