In an era where cyberattacks, data breaches, and identity theft are increasingly common, traditional authentication methods are no longer
enough. Passwords can be guessed, stolen, or cracked. Multifactor Authentication (MFA) introduces a much-needed layer of security, making it
drastically harder for unauthorized users to gain access to sensitive systems.
What is Multifactor Authentication (MFA)?
Multifactor Authentication (MFA) is a security technique that requires a user to verify their identity using two or more
independent credentials before they can access a system, application, or network. These credentials must come from distinct categories, making it exponentially more difficult for attackers to gain access even if one factor is compromised.
MFA is built on the principle that no single factor (like a password) is strong enough on its own. By combining different forms of authentication, organizations can minimize the risk of fraud, unauthorized access, and data loss.
For example:
When logging into an email account, instead of just using a password, you also need to enter a code sent to your mobile device. That’s MFA in action.
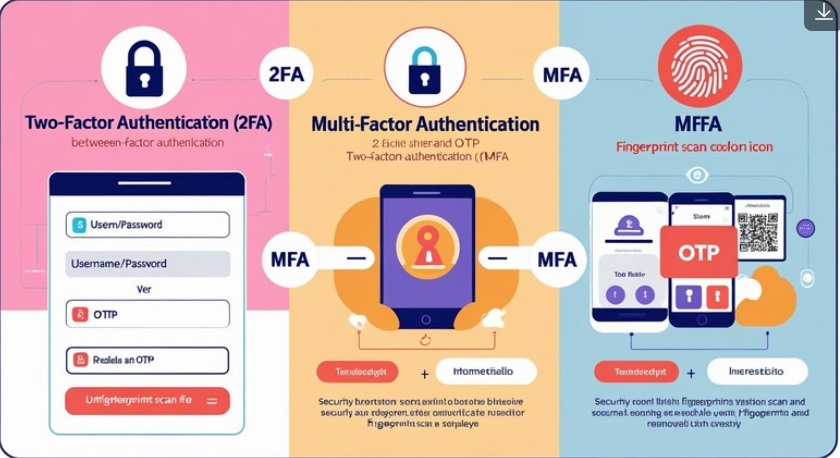
What is Two-Factor Authentication (2FA)?
Two-Factor Authentication (2FA) is a type of MFA that requires exactly two of the following factors for authentication:
- Factor1: Your regular login credentials (username and password)
- Factor2: A second verification method, such as an OTP sent via SMS or a biometric scan
Difference between 2FA and MFA:
- 2FA always involves only two factors.
- MFA may involve two or more, such as combining password + OTP + fingerprint for extremely secure systems.
While 2FA is a good starting point, MFA offers more flexibility and stronger security by incorporating multiple layers.
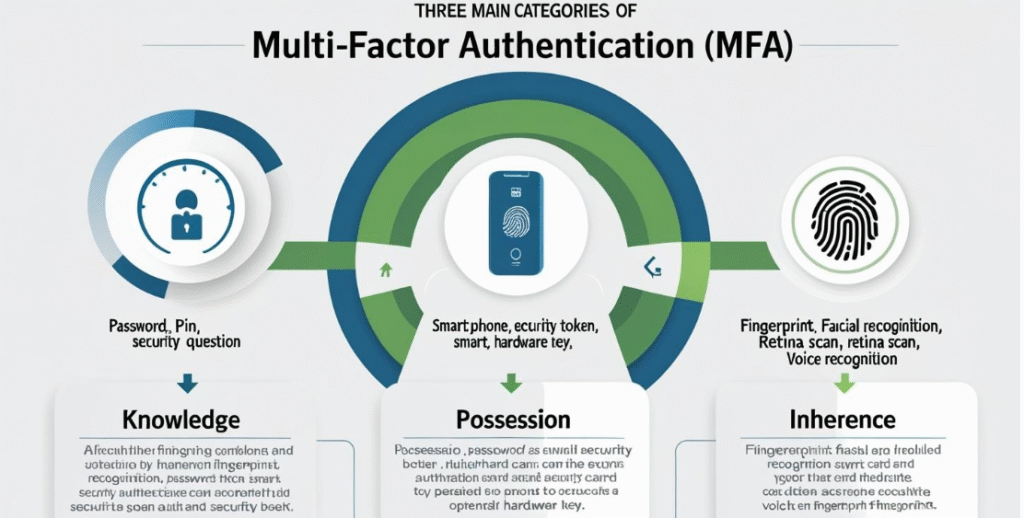
Types of MFA Factors
Each authentication factor must be independent and belong to a different category. Here are the three main types of MFA factors:
- A password, PIN, or answer to a security question
- This is the most common and weakest factor because it can be easily stolen or guessed
- A smartphone, security token, smart card, or hardware key
- This adds a physical barrier that attackers need to possess
- Biometrics, such as fingerprints, facial recognition, retina scans, or voice recognition
- This is difficult to replicate, making it one of the most secure options
- Somewhere You Are: Based on geolocation or IP address
- Something You Do: Behavioral patterns like typing rhythm or mouse movements
By combining these types, MFA offers a layered defense system that makes unauthorized access highly unlikely.
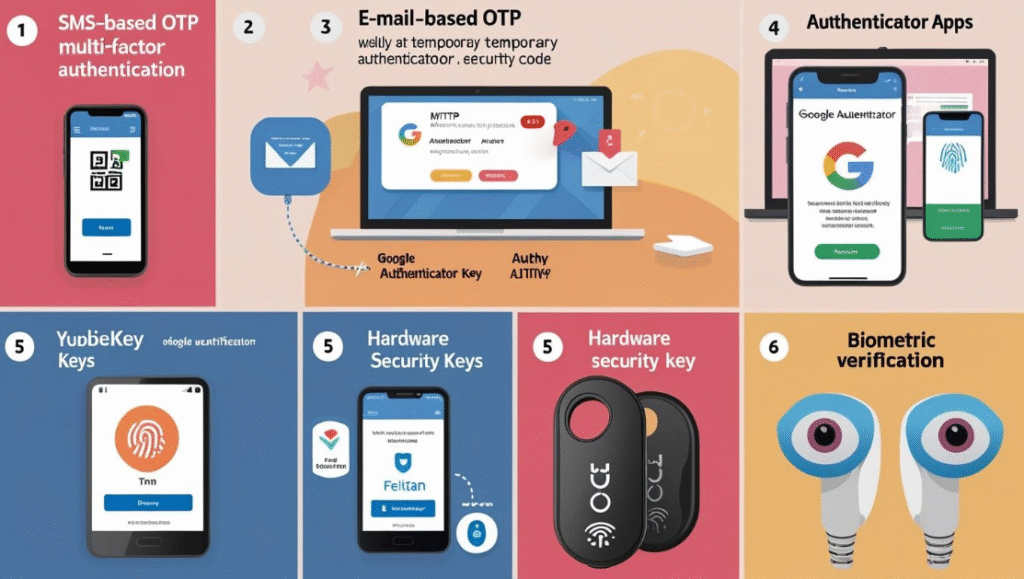
Common Methods of MFA
Here are some widely adopted methods used in implementing MFA:
1. SMS-based One-Time Password (OTP)
- A temporary code is sent to the user’s mobile phone.
- Must be entered within a limited time window.
- Risk: SMS can be intercepted via SIM swapping or malware.
- A code is emailed to the registered email address.
- Often used for low-risk scenarios or recovery.
- Mobile apps like Google Authenticator, Microsoft Authenticator, or Authy generate time-based one-time passwords (TOTP).
- More secure than SMS since it works offline and can’t be intercepted.
- When logging in, a push is sent to a mobile device prompting the user to “Approve” or “Deny.”
- Fast, simple, and user-friendly.
- Often combined with biometrics for stronger protection.
- Physical USB or NFC devices like YubiKey, Feitian, or Google Titan Key.
- Can be used to authenticate without relying on passwords.
- Scans of fingerprints, face, or iris to confirm the user’s identity.
Popular in high-security environments and smartphones (e.g., Face ID, Touch ID)
Real-World Examples of MFA
Let’s explore a few in-depth scenarios where MFA is applied:
Example 1: Microsoft 365 Login with MFA
- A user logs into Microsoft 365 using their email and password.
- They receive a push notification on the Microsoft Authenticator app.
- To approve, they must also complete biometric verification (like Face ID).
Factors used:
- Something you know – Password
- Something you have – Phone with Authenticator
- Something you are – Face ID
➡️ This combination provides very strong identity assurance.
Example 2: Online Banking Portal Access
- The
user enters username and password.
- An OTP
is sent to their registered mobile number.
- In
some cases, users must also answer a pre-set security question.
Factors used:
- Something
you know – Password & security question
- Something
you have – OTP on mobile device
➡️ Common in the financial
sector, where compliance and fraud protection are critical.
Example 3: Secure Enterprise System Login
- Employees
insert a smart ID card into a card reader.
- Enter
a PIN code.
- Perform
a fingerprint scan for biometric verification.
Factors used:
- Something
you have – Smart card
- Something
you know – PIN
- Something
you are – Fingerprint
➡️ This setup is ideal for government or defense environments with strict security requirements.
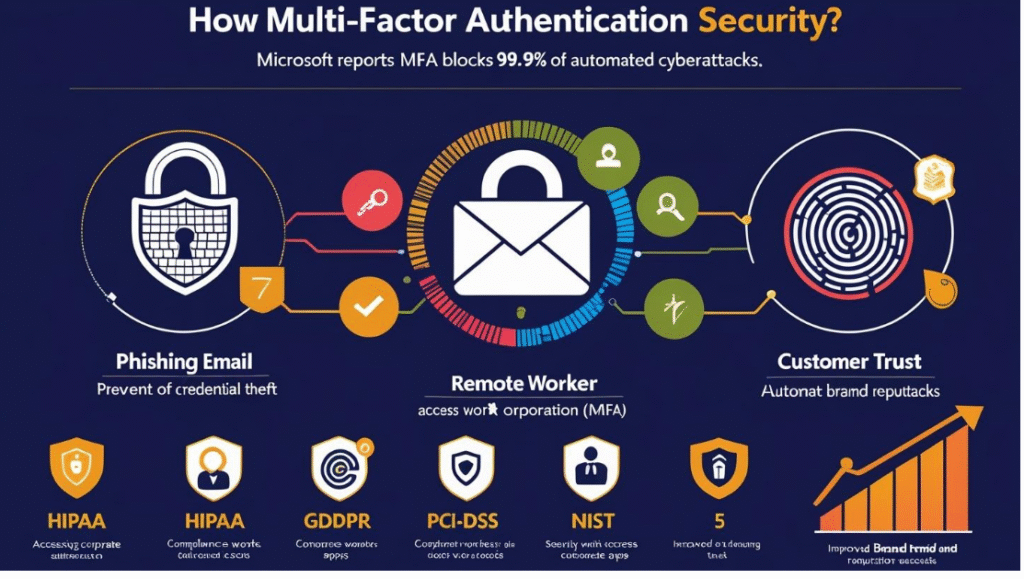
How MFA Enhances Security
Here’s how MFA greatly improves cybersecurity:
1. Prevents Credential Theft
- Even
if your password is leaked or guessed, an attacker still needs the second
factor (e.g., OTP or fingerprint).
2. Reduces Impact of Phishing
- Phishing
emails often steal credentials, but they rarely capture second-factor data
like app-based codes or biometrics.
3. Ensures Compliance
- Regulatory
standards like HIPAA, GDPR, PCI-DSS, and NIST
require or strongly recommend MFA for sensitive data protection.
4. Protects Remote Workforces
- With
more employees working remotely, MFA ensures that only legitimate users
can access corporate apps and cloud environments.
5. Builds Customer Trust
- Companies
that use MFA signal to their users that security is a priority,
boosting brand reputation and trustworthiness.
Microsoft reports that enabling MFA can block 99.9% of
automated cyberattacks.
Conclusion
Multifactor Authentication is no longer optional—it’s
essential. It dramatically reduces the risk of data breaches, account
takeovers, and unauthorized access. Whether you’re securing personal email,
enterprise software, or customer-facing portals, MFA provides an invisible
yet powerful barrier between your data and cybercriminals.
By leveraging combinations of passwords, devices, and
biometrics, MFA makes your systems vastly more secure without
sacrificing user convenience.












Leave a Reply