Integrating SCIM provisioning with an IT Asset Management (ITAM) platform like Reftab streamlines operations by automating the process of user account creation, updates, and deactivation. This ensures that asset assignments are managed accurately and promptly. Additionally, it boosts security and compliance by keeping user information synchronized across systems, minimizing the chances of unauthorized access or data discrepancies.
1. Sign in to Azure, search for “Entra ID,” and select “Microsoft Entra ID” from the results.
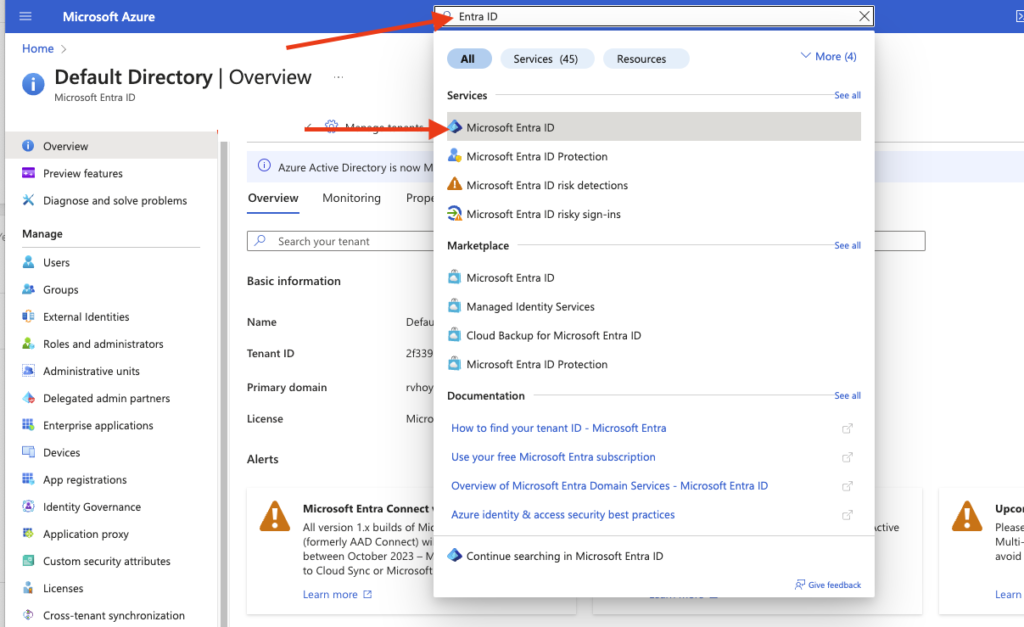
2 – Click “Enterprise Applications”
3 Now Click on “New Application” on the top
4 – “Create your own application”
5 –Enter Name your application
6 – In the new app, click Provision User Accounts
7 – Get Started
8 — Set the provisioning mode to automatic. Enter the Tenant URL and secret token provided in your Test account. Then, log in to Test as an administrator, navigate to “Settings” > “Integrations,” and click “Configure” next to SCIM.
9 — Copy Endpoint and paste it into “Tenant URL” in Azure
Copy Token and paste it into “Secret Token” in Azure.
10 — Finally,
click “Test Connection” and “Save”.
11 – Go to Provision Azure Active Directory User Mappings to check mappings.
12 – Setup Attribute mapping accordingly, as shown in the image below.
13 – Mail attribute must be mapped to username with matching precedence of 1.
14 – Turn on provisioning status in the app, then click save on the top.
15 — Add any users and or groups you want to be sent to the application.
16 – Log into application . Click “Settings” > “Integrations” > “Configure SCIM”.
17 — Next, configure role assignments.
NOTE ON MULTI-TENANCY:
If you are using multi-tenancy with Test, you can manage users/groups and sync them to their respective tenants. To do this, set up SCIM at the super tenant level. This allows for a one-to-many relationship, letting you push users and groups into separate tenants from the super tenant without having to log into each individual tenant. For assistance, please contact Test support by emailing “help@test.com.”
Default Test Access Role:
This is the default role assigned to users from Entra who do not belong to any Entra group.
Group Mappings:
In this section, you can view the groups being pushed from Entra into Test. You can also map Test access roles to these groups. For example, if you push a group called “Employees” into Test, every user transferred from that group can be assigned a corresponding role.
18 — Notes:
Sync Frequency
Users should begin appearing on the “Sub Accounts” page in Test. Subsequent syncs are triggered every 20-40 minutes.
Disabled Users
If a user was part of a group pushed to Test but later removed from that group, they will be assigned the “Default Role (for SCIM users without groups)” on the next sync. Additionally, if a user is disabled in Microsoft Azure, Test will recognize this and mark the user as “Disabled” in Test during the sync.
Role Lock
To lock users into a specific Test access role (for example, users who should be Test administrators), enable the “role-lock” feature in Test. This setting locks the user into their current role, preventing changes during syncs even if their group changes in MS Entra or role assignment rules are modified in Test. Essentially, enabling this feature bypasses role assignments and ensures the user remains in their designated role.
Conclusion:
Setting up SCIM with Microsoft Entra ID (Azure Active Directory) and integrating it with an IT asset management system like Test offers significant benefits, including streamlined user account management, enhanced security, and improved operational efficiency. By automating the creation, update, and deactivation of user accounts, organizations can ensure that asset assignments are always accurate and up-to-date, while also reducing the risk of errors and unauthorized access. The ability to configure multi-tenancy, manage user roles, and synchronize user data across platforms provides a robust solution for maintaining compliance and operational integrity. Overall, leveraging SCIM provisioning is a powerful way to optimize user and asset management processes, ensuring seamless integration between systems and greater control over user data.





Leave a Reply