Conditional Access in Microsoft Entra ID: (2026 Edition)
Description: Conditional Access in Microsoft Entra ID explained in a 30,000-word mega guide covering Zero Trust, policies, monitoring, troubleshooting, PowerShell, Graph API and real-world implementation.
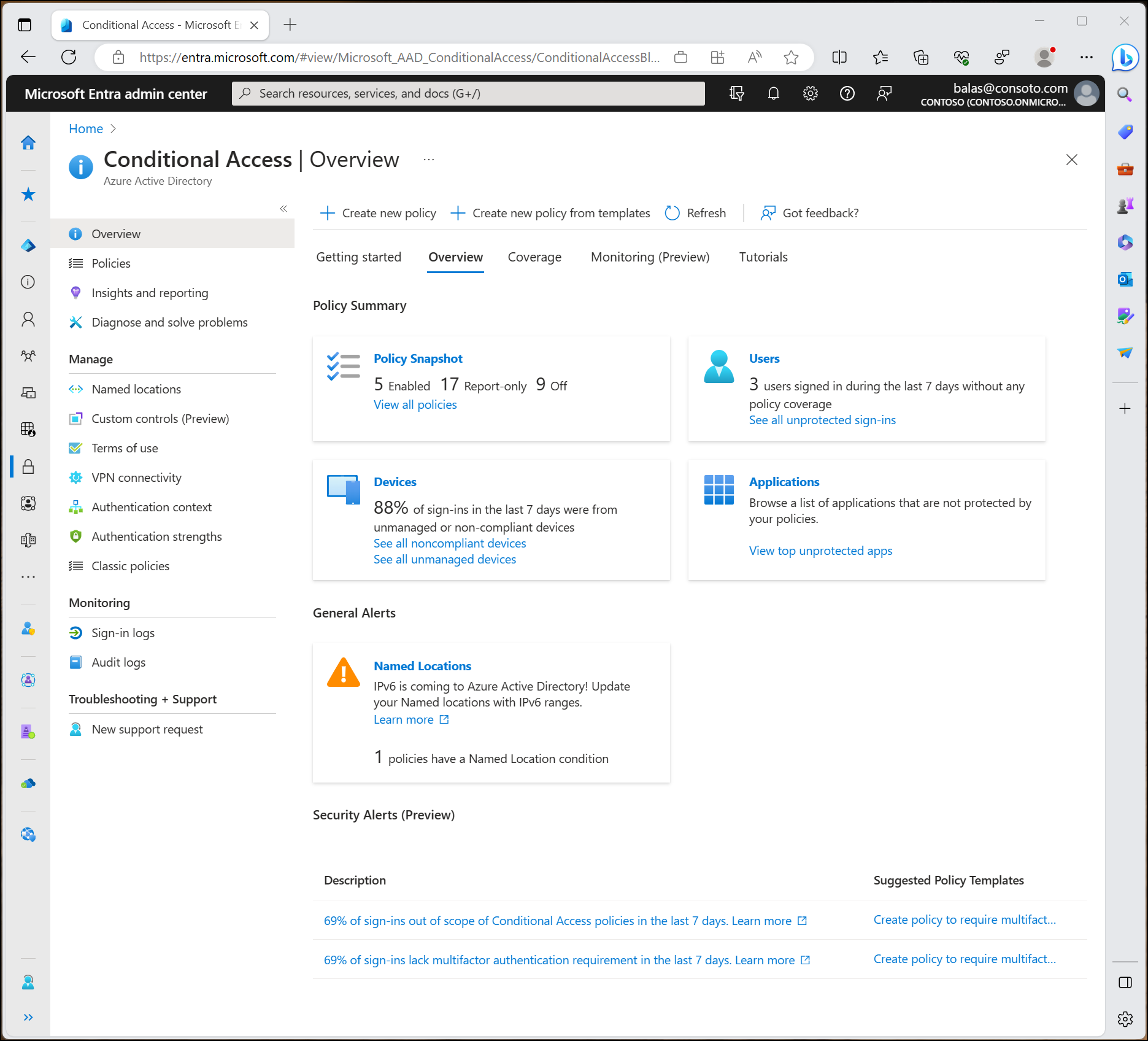
Conditional Access in Microsoft Entra ID – Complete Overview
Conditional Access in Microsoft Entra ID is Microsoft’s Zero Trust policy engine that evaluates user identity, device state, location, application, and risk signals before granting or blocking access to enterprise resources.
It works on a powerful decision model:
IF signals match specific conditions → THEN apply access controls.
This model enables organizations to implement modern security architecture without relying solely on passwords.
What is Conditional Access?
Conditional Access is a security framework inside Microsoft Entra Admin Center that dynamically enforces policies during authentication.
It replaces legacy per-app access rules with centralized identity-based governance.
Core Signals Evaluated
- User or Group Membership
- Directory Role
- Application Access
- Device Compliance
- Hybrid Join Status
- IP Address & Named Location
- Sign-in Risk Level
- User Risk Level
Zero Trust Architecture Explained
Conditional Access in Microsoft Entra ID is built on the Zero Trust principle:
Never Trust. Always Verify.
Zero Trust assumes breach and validates every access attempt.
For deeper understanding of Zero Trust, refer to Microsoft’s official architecture guidance:
Microsoft Zero Trust Framework
Why Conditional Access is Critical in 2026
Modern threats include:
- Password spray attacks
- Token theft
- Session hijacking
- Legacy protocol abuse
- Phishing campaigns
Conditional Access mitigates these risks through:
- MFA enforcement
- Authentication strengths
- Device compliance validation
- Risk-based access
- Blocking legacy authentication
Conditional Access vs Legacy MFA
| Feature | Legacy MFA | Conditional Access |
|---|---|---|
| App-based control | No | Yes |
| Location-based logic | No | Yes |
| Device compliance | No | Yes |
| Risk-based evaluation | No | Yes |
Conditional Access Architecture Flow
- User attempts login
- Authentication request hits Entra ID
- Signals collected
- Policy evaluation engine runs
- Grant or Block decision applied
- Session created
- Logs written
Key Components of Conditional Access
Assignments
- Users & Groups
- Directory Roles
- Applications
Conditions
- Sign-in Risk
- User Risk
- Device Platform
- Locations
- Client Apps
Access Controls
- Require MFA
- Require compliant device
- Block access
- Authentication strength
Internal Resource for Advanced Entra Topics
For additional implementation guides, visit:
Conditional Access Policy Deep Dive Guide
Frequently Asked Questions – Foundations
Is Conditional Access available in all licenses?
No. It requires Microsoft Entra ID P1 or P2 licensing.
Can Conditional Access block specific countries?
Yes. Using Named Locations and country-based rules.
Is Conditional Access applied after authentication?
Yes. It evaluates after primary authentication but before token issuance.
Key Takeaways from Part 1
- Conditional Access in Microsoft Entra ID is the core of Zero Trust
- It evaluates multiple signals dynamically
- It replaces legacy MFA approaches
- It centralizes enterprise security policies
Conditional Access in Microsoft Entra ID – IF → THEN Policy Logic Explained
Conditional Access in Microsoft Entra ID works on a powerful evaluation model:
IF specific signals are true → THEN enforce access controls.
This decision-based architecture allows identity-driven enforcement instead of network perimeter security.
How the Policy Engine Evaluates Access
- User initiates authentication
- Primary authentication validates credentials
- Signals are collected (device, location, risk, app)
- All enabled Conditional Access policies are evaluated
- If conditions match → Grant controls enforced
- Access token issued or blocked
Official Microsoft documentation for evaluation logic:
Conditional Access policy evaluation logic (Microsoft Docs)
Conditional Access in Microsoft Entra ID – Policy Structure Breakdown
1️⃣ Assignments (WHO + WHAT)
Assignments determine:
- Which users or groups are included
- Which directory roles are targeted
- Which cloud applications are affected
Users & Groups
- All Users
- Specific Groups
- Directory Roles (Global Admin, Security Admin)
- Guest or External Users
Best Practice: Always exclude at least two emergency break-glass accounts.
Learn more about emergency access strategy:
Emergency access accounts guidance
2️⃣ Target Resources (Applications)
Conditional Access can target:
- All cloud apps
- Office 365 apps
- Specific Enterprise Applications
- Authentication Context
Example scenario:
- Require stronger MFA for Azure Portal
- Block risky login for Exchange Online
Internal reference for application registration:
Azure AD App Registration & SSO Guide
3️⃣ Conditions (WHEN)
Conditions are the intelligence layer of Conditional Access in Microsoft Entra ID.
Available Conditions
- Sign-in Risk
- User Risk
- Device Platform
- Locations
- Client Apps
- Filter for Devices
Sign-in Risk Condition
Evaluates real-time risk during authentication using Microsoft Defender signals.
- Low
- Medium
- High
Requires Entra ID P2 license.
Official reference:
Microsoft Identity Protection Overview
User Risk Condition
Evaluates long-term compromise likelihood.
Example:
- If user risk = High → Force password reset
Device Platform Condition
- Windows
- macOS
- iOS
- Android
- Linux
Use case:
- Block access from Linux devices
- Require compliant device for Windows
Locations Condition
Uses Named Locations to differentiate:
- Trusted IP ranges
- Blocked countries
- External networks
Internal guide:
Named Locations Configuration Guide
Client Apps Condition
Used primarily to block legacy authentication:
- Exchange ActiveSync
- Other legacy protocols
Blocking legacy authentication is one of the most important steps in securing Conditional Access in Microsoft Entra ID.
4️⃣ Access Controls (THEN)
This is the enforcement layer.
Grant Controls
- Require Multi-Factor Authentication
- Require compliant device
- Require hybrid Azure AD joined device
- Require authentication strength
- Block access
Session Controls
- Sign-in frequency
- Persistent browser
- App enforced restrictions
Policy Evaluation Order in Conditional Access
All enabled policies are evaluated independently.
If ANY policy blocks access → Access is denied.
If multiple policies apply → All required grant controls must be satisfied.
Example
- Policy 1 → Require MFA
- Policy 2 → Require compliant device
User must complete BOTH requirements.
Report-Only Mode Explained
Report-only mode allows simulation before enforcement.
Benefits:
- Measure impact
- Avoid production outage
- Test safely
Always deploy new Conditional Access policies in Report-only mode first.
PowerShell – Viewing Conditional Access Policies
Install Microsoft Graph module:
Install-Module Microsoft.Graph -Scope CurrentUser Connect-MgGraph -Scopes "Policy.Read.All" Get-MgIdentityConditionalAccessPolicy
This retrieves all Conditional Access policies in Microsoft Entra ID.
Graph API – Retrieve Conditional Access Policies
GET https://graph.microsoft.com/v1.0/identity/conditionalAccess/policies
Requires:
- Policy.Read.All
- Directory.Read.All
Official API reference:
Conditional Access Graph API Reference
Common Policy Design Mistakes
- Not excluding emergency account
- Enabling policy directly without report-only
- Overlapping block rules
- Incorrect IP range in Named Locations
- Forgetting device compliance dependency
FAQs – Policy Deep Dive
Do policies have priority order?
No traditional priority. All policies evaluate simultaneously.
Can Conditional Access require multiple controls?
Yes. Use "Require all selected controls" option.
Does Conditional Access replace firewall security?
No. It complements network security with identity-based enforcement.
Can I automate policy creation?
Yes. Using Microsoft Graph API or PowerShell.
Key Takeaways from Part 2
- Conditional Access in Microsoft Entra ID uses IF → THEN logic
- Assignments define WHO
- Conditions define WHEN
- Access controls define WHAT happens
- All policies evaluate independently
- Report-only mode prevents production outages
Conditional Access in Microsoft Entra ID – Named Locations Deep Dive
Conditional Access in Microsoft Entra ID becomes significantly more powerful when combined with Named Locations. Named Locations allow administrators to define trusted IP ranges or countries and use them as decision signals inside Conditional Access policies.
What Are Named Locations?
Named Locations are logical representations of:
- Corporate Office IP ranges
- Trusted VPN networks
- Blocked high-risk countries
- Specific geographic regions
They are configured inside:
Entra Admin Center → Protection → Conditional Access → Named Locations
Official Microsoft documentation:
Location condition in Conditional Access
Types of Named Locations
1️⃣ IP Range Based Location
- Static Public IP
- Multiple CIDR blocks
- Trusted flag option
2️⃣ Country-Based Location
- Select specific countries
- Block high-risk regions
Best Practice for Named Locations
- Verify public IP before configuration
- Use “Trusted” flag only for secure networks
- Review quarterly
- Document IP ownership
PowerShell – Retrieve Named Locations
Connect-MgGraph -Scopes "Policy.Read.All" Get-MgIdentityConditionalAccessNamedLocation
Graph API – Get Named Locations
GET https://graph.microsoft.com/v1.0/identity/conditionalAccess/namedLocations
Conditional Access in Microsoft Entra ID – Authentication Strengths
Authentication Strengths define the quality of authentication required.
Why Authentication Strengths Matter
Not all MFA methods are equal.
- SMS = weaker
- FIDO2 = phishing-resistant
- Certificate-based authentication = high assurance
Authentication Strength policies allow administrators to enforce stronger verification methods for high-value accounts.
Official documentation:
Authentication Strengths Overview
Built-in Authentication Strength Options
- Password + SMS
- Password + Microsoft Authenticator
- Phishing-resistant MFA
Phishing-Resistant MFA Includes
- FIDO2 security keys
- Certificate-based authentication
- Windows Hello for Business
Use Case Example
Policy:
- If user is Global Administrator
- Then require phishing-resistant MFA
Graph API – Authentication Strength Policy
GET https://graph.microsoft.com/v1.0/policies/authenticationStrengthPolicies
Authentication Context in Conditional Access
Authentication Context enables step-up authentication for specific applications or resources.
Example Scenario
- SharePoint site contains financial reports
- Require stronger authentication only for that site
Authentication Context is mapped to app resources.
Official reference:
Authentication Context in Conditional Access
Terms of Use in Conditional Access
Terms of Use allows organizations to require users to accept compliance or security policies before accessing resources.
Common Use Cases
- BYOD device access acceptance
- Legal policy acknowledgment
- Data protection agreement
Users must accept the document before access is granted.
VPN Connectivity and Conditional Access
Conditional Access integrates with VPN solutions to enforce identity-based verification before network connection is established.
Modern Approach
- Azure VPN + Conditional Access
- Third-party VPN with SAML integration
Classic Policies vs Conditional Access
Legacy MFA and per-user MFA policies are deprecated.
Conditional Access provides:
- Granular targeting
- Application-based enforcement
- Risk-based policies
- Authentication strengths
Migration guidance:
Migrate from per-user MFA to Conditional Access
Advanced Design Pattern – Tiered Security Model
Tier 0 – Admin Accounts
- Require phishing-resistant MFA
- Require compliant device
- Block outside trusted location
Tier 1 – Power Users
- Require MFA
- Block legacy authentication
Tier 2 – Standard Users
- Require MFA outside trusted network
Internal Deep-Dive Resource
Explore more enterprise-level Entra configuration at:
FAQs – Named Locations & Authentication Strengths
Can I combine Named Location with Authentication Strength?
Yes. Example: Require phishing-resistant MFA outside corporate network.
Can Authentication Strength override MFA requirement?
Authentication Strength enhances MFA by restricting allowed methods.
Is Terms of Use mandatory?
No. It is optional but recommended for compliance.
Does country-based blocking stop VPN bypass?
No. Advanced attackers can use VPNs; combine with risk-based policies.
Key Takeaways from Part 3
- Named Locations define trusted or blocked regions
- Authentication Strength improves MFA security
- Authentication Context enables step-up security
- Terms of Use enforces compliance acceptance
- Classic MFA policies should be migrated
Conditional Access in Microsoft Entra ID – Monitoring & Sign-in Logs Deep Dive
Conditional Access in Microsoft Entra ID is only as effective as your ability to monitor and troubleshoot it. Many organizations deploy strong policies but fail to actively monitor sign-in behavior, which creates blind spots.
Monitoring allows administrators to:
- Identify blocked users
- Detect risky sign-ins
- Validate policy impact
- Troubleshoot authentication failures
- Audit configuration changes
Sign-in Logs in Conditional Access
Sign-in logs are the primary troubleshooting tool for Conditional Access in Microsoft Entra ID.
Navigate to:
Entra Admin Center → Monitoring → Sign-in Logs
Official documentation:
Microsoft Entra sign-in logs documentation
What Information Sign-in Logs Show
- User identity
- Application accessed
- Client app type
- Device details
- Location (IP + country)
- Risk level
- Conditional Access result
Conditional Access Tab Inside Sign-in Logs
Click any sign-in event → Open Conditional Access tab.
This section shows:
- Applied policies
- Policies not applied
- Grant controls enforced
- Failure reason
This is the fastest way to troubleshoot access issues.
Common Sign-in Result Types
| Result | Meaning |
|---|---|
| Success | Access granted |
| Failure | Blocked by policy |
| Interrupted | Session expired or MFA failed |
| Report-only | Simulation mode applied |
Audit Logs in Conditional Access
Audit logs track configuration changes in Conditional Access in Microsoft Entra ID.
Navigate to:
Entra Admin Center → Monitoring → Audit Logs
Audit logs record:
- Policy creation
- Policy modification
- Policy deletion
- Named Location changes
- Authentication strength updates
Official documentation:
Microsoft Entra audit logs documentation
Insights and Reporting in Conditional Access
Insights and Reporting provides aggregated analysis of policy impact.
It helps answer:
- How many users are affected?
- Which policies cause most failures?
- Which apps trigger MFA most frequently?
Always use Report-only mode before enforcement to review Insights data.
Diagnose and Solve Problems Tool
This built-in tool simplifies troubleshooting.
Steps:
- Go to Conditional Access
- Select Diagnose and Solve Problems
- Enter user
- Select application
- Run diagnostic
It provides:
- Matching policies
- Blocking conditions
- Recommended fixes
Log Analytics Integration for Advanced Monitoring
For enterprise environments, integrate sign-in logs with Azure Monitor or Sentinel.
Enable diagnostic settings:
- Send logs to Log Analytics workspace
- Export to Event Hub
- Archive to Storage account
Official guidance:
Integrate Entra logs with Log Analytics
KQL Queries for Conditional Access Troubleshooting
Find Blocked Sign-ins
SigninLogs | where ConditionalAccessStatus == "failure" | project TimeGenerated, UserPrincipalName, AppDisplayName, IPAddress | order by TimeGenerated desc
Find MFA Failures
SigninLogs | where AuthenticationRequirement == "multiFactorAuthentication" | where ResultType != 0 | project TimeGenerated, UserPrincipalName, ResultDescription
Find Sign-ins from Suspicious Countries
SigninLogs
| where LocationDetails.countryOrRegion !in ("India","United States")
| project TimeGenerated, UserPrincipalName, LocationDetails
PowerShell – Export Sign-in Logs
Connect-MgGraph -Scopes "AuditLog.Read.All" Get-MgAuditLogSignIn -Top 50
Graph API – Retrieve Sign-in Logs
GET https://graph.microsoft.com/v1.0/auditLogs/signIns
Requires:
- AuditLog.Read.All
- Directory.Read.All
Real-World Troubleshooting Scenarios
Scenario 1 – User Blocked Unexpectedly
Steps:
- Check sign-in logs
- Open Conditional Access tab
- Identify blocking policy
- Review location & device state
Scenario 2 – MFA Not Triggering
- Policy in report-only?
- Correct user targeted?
- Location misconfigured?
- Authentication strength restricting method?
Scenario 3 – Admin Lockout
- Use emergency account
- Disable problematic policy
- Review exclusions
Internal Resource for Troubleshooting
Conditional Access Troubleshooting Guide
Security Monitoring Best Practices
- Review sign-in logs daily
- Monitor high-risk users weekly
- Enable log retention for 90+ days
- Integrate with SIEM
- Enable alerts for admin login
FAQs – Monitoring & Logs
How long are sign-in logs retained?
Default 7–30 days depending on license. Extended retention requires Log Analytics.
Can I alert on specific Conditional Access failures?
Yes, using Azure Monitor alerts with KQL queries.
Does report-only show in logs?
Yes. It shows “Report-only” status in Conditional Access tab.
Can attackers hide from sign-in logs?
No. Every authentication attempt is logged.
Key Takeaways from Part 4
- Sign-in logs are primary troubleshooting tool
- Audit logs track configuration changes
- Insights help evaluate policy impact
- KQL enables advanced detection
- Log Analytics integration improves visibility
Conditional Access in Microsoft Entra ID – Real-World Policy Implementation
Conditional Access in Microsoft Entra ID becomes powerful when translated from theory into production-ready policies. In this section, we will design, configure, test, and safely deploy three enterprise-grade Conditional Access policies used in real environments.
Policy 1 – Block Legacy Authentication (Critical Security Control)
Legacy authentication protocols (POP, IMAP, SMTP AUTH, Exchange ActiveSync basic auth) do not support modern MFA. Attackers frequently exploit these protocols for password spray attacks.
Official Microsoft guidance:
Block legacy authentication using Conditional Access
Step-by-Step Configuration
- Go to Entra Admin Center
- Navigate to Protection → Conditional Access
- Click “+ New Policy”
- Name: CA – Block Legacy Authentication
Assignments
- Users → Include: All Users
- Exclude → Break-glass emergency accounts
Target Resources
- All Cloud Apps
Conditions
- Client Apps → Select:
- Exchange ActiveSync
- Other clients
Grant Controls
- Block Access
Enable Policy
- Start in Report-only mode
- Monitor for 7 days
- Then switch to On
Testing Scenario
- Attempt login via old Outlook client
- Check Sign-in logs
- Verify Conditional Access result: Failure
Common Mistakes
- Not enabling modern authentication globally
- Blocking service accounts accidentally
- Forgetting exclusions
Policy 2 – Require MFA Outside Trusted Location
This policy enforces MFA only when users authenticate outside corporate IP ranges.
Step 1 – Configure Named Location
- Conditional Access → Named Locations
- Create new location
- Name: Corporate Office
- Add public IP range
- Mark as Trusted
Internal reference:
Named Location Configuration Guide
Step 2 – Create Conditional Access Policy
- Click “+ New Policy”
- Name: CA – Require MFA Outside Trusted Location
Assignments
- Include: All Users
- Exclude: Emergency accounts
Target Resources
- All Cloud Apps
Conditions
- Locations → Include: Any location
- Exclude: Corporate Office
Grant
- Require Multi-Factor Authentication
Enable
- Report-only first
- Review logs
- Enable fully
Testing Scenarios
Test 1 – Inside Corporate IP
- No MFA prompt expected
Test 2 – Outside Corporate IP
- MFA prompt expected
Production Tip
Combine with Authentication Strength to prevent weak MFA methods like SMS for high-risk users.
Policy 3 – Admin Protection Policy (High Security Tier)
Administrators represent Tier-0 security assets. Compromise of these accounts leads to full tenant breach.
Official guidance:
Step-by-Step Configuration
- Create new policy
- Name: CA – Admin Protection Policy
Assignments
- Select Directory Roles:
- Global Administrator
- Security Administrator
- Application Administrator
Target Resources
- All Cloud Apps
Conditions
- Locations → Any
- Device Platform → Any
Grant Controls
- Require Multi-Factor Authentication
- Require Compliant Device
- Require All Selected Controls
Optional Advanced
- Authentication Strength → Phishing-resistant MFA
Testing Admin Policy
- Login from non-compliant device
- Access should be blocked
- Verify logs for failure reason
Change Management & Rollout Strategy
Recommended Deployment Approach
- Design policy
- Enable Report-only
- Review Insights data
- Communicate to users
- Enable during low-usage hours
- Monitor logs closely for 48 hours
Policy Conflict Scenarios
Scenario: User Blocked Even After MFA
Possible cause:
- Another policy requiring compliant device
Scenario: MFA Prompt Not Appearing
- Policy in report-only
- Authentication strength restriction
PowerShell – Export Conditional Access Policies
Connect-MgGraph -Scopes "Policy.Read.All" Get-MgIdentityConditionalAccessPolicy | Format-List
Graph API – Create Conditional Access Policy
POST https://graph.microsoft.com/v1.0/identity/conditionalAccess/policies
Requires:
- Policy.ReadWrite.ConditionalAccess
FAQs – Real-World Policies
Should every tenant block legacy authentication?
Yes. It is one of the most important security controls.
Is location-based MFA secure?
Yes, when combined with device compliance and authentication strength.
Should admin accounts use SMS MFA?
No. Use phishing-resistant MFA methods.
How long should report-only mode run?
Minimum 5–7 days in production.
Key Takeaways from Part 5
- Block legacy authentication first
- Use location-based MFA policies
- Protect admin roles separately
- Always test before enforcement
- Monitor logs during rollout
Conditional Access in Microsoft Entra ID – Advanced Admin Protection Architecture
Conditional Access in Microsoft Entra ID must be designed differently for privileged accounts. Administrators represent Tier-0 assets, and their compromise leads to complete tenant takeover.
Why Admin Protection Requires Special Design
- Admins have access to security settings
- Admins can modify Conditional Access policies
- Admins can elevate permissions
- Admins can access sensitive audit data
Official Microsoft privileged access guidance:
Microsoft Privileged Access Model
Recommended Tiered Admin Controls
Tier 0 – Global Administrators
- Phishing-resistant MFA required
- Compliant device mandatory
- Block outside trusted locations
- Privileged Access Workstation recommended
Tier 1 – App & Security Admins
- MFA mandatory
- Device compliance required
- Restricted sign-in frequency
Conditional Access in Microsoft Entra ID – Risk-Based Policies
Risk-based Conditional Access policies use Microsoft Identity Protection signals to dynamically evaluate risk levels.
These policies require Entra ID P2 licensing.
Official reference:
Sign-in Risk Policy
Evaluates login attempt in real time.
- Low risk
- Medium risk
- High risk
Example Policy
- If Sign-in Risk = Medium or High
- Then Require MFA
User Risk Policy
Evaluates long-term account compromise likelihood.
Example Policy
- If User Risk = High
- Then Require Password Change
Device Compliance Integration with Intune
Conditional Access integrates with Microsoft Intune to validate device health.
Official documentation:
Intune + Conditional Access integration
Device Compliance Checks Include
- OS version
- Antivirus status
- Disk encryption
- Secure boot enabled
- Jailbreak/root detection
Example Device-Based Policy
- Users: All users
- Condition: Device platform Windows
- Grant: Require compliant device
Hybrid Azure AD Joined Device Policy
Organizations with on-prem Active Directory can require Hybrid Join status.
Example
- If device is not Hybrid Azure AD joined
- Then Block Access
This ensures only domain-managed devices access corporate apps.
Conditional Access for B2B & Guest Users
External collaboration increases risk exposure.
Conditional Access in Microsoft Entra ID allows specific targeting of guest accounts.
Recommended Guest Policy
- Users: All guest users
- Grant: Require MFA
- Block legacy authentication
- Restrict to specific applications
Official documentation:
Conditional Access for B2B users
Tiered Access Architecture Model
Tier 0 – Identity & Security
- Admins
- Domain controllers
- Azure AD Connect
Tier 1 – Servers & Applications
- App servers
- Database servers
Tier 2 – End Users
- Standard employees
- Contractors
Conditional Access policies should reflect this tier separation.
Advanced Conditional Access Design Pattern
Combine Risk + Location + Device
Example:
- If Sign-in Risk = Medium
- AND Location = Outside Trusted IP
- AND Device not compliant
- Then Block Access
This layered approach significantly improves Zero Trust posture.
Session Controls for Sensitive Applications
- Sign-in frequency = 8 hours
- Disable persistent browser
- App enforced restrictions
Internal Advanced Guides
Enterprise Conditional Access Strategy
Common Advanced Design Mistakes
- Applying admin-level controls to all users
- Ignoring device compliance dependencies
- Not separating Tier 0 policies
- Forgetting guest user enforcement
FAQs – Advanced Policies
Do risk-based policies replace MFA policies?
No. They complement baseline MFA requirements.
Should guest users be treated like internal users?
No. Apply stricter controls for guests.
Can device compliance override risk?
No. Risk signals are independent and evaluated separately.
Is Hybrid Join required for all tenants?
Only if on-prem Active Directory integration exists.
Key Takeaways from Part 6
- Admin accounts require strongest controls
- Risk-based policies enhance dynamic protection
- Device compliance adds endpoint validation
- Tiered access model improves segmentation
- Guest users require separate policies
Conditional Access in Microsoft Entra ID – Automation & DevOps Strategy
Conditional Access in Microsoft Entra ID should not be managed manually in large enterprises. Modern identity governance requires automation, version control, backup, and CI/CD deployment models.
This section covers:
- PowerShell automation
- Microsoft Graph API management
- Policy backup & restore
- JSON policy structure
- Infrastructure-as-Code approach
Why Automate Conditional Access?
- Prevent configuration drift
- Enable disaster recovery
- Standardize multi-tenant deployment
- Track changes via version control
- Reduce human error
Official Microsoft Graph documentation:
Microsoft Graph – Conditional Access API
PowerShell – Connect to Microsoft Graph
Install-Module Microsoft.Graph -Scope CurrentUser Connect-MgGraph -Scopes "Policy.ReadWrite.ConditionalAccess","Directory.Read.All"
Export All Conditional Access Policies (Backup)
$policies = Get-MgIdentityConditionalAccessPolicy $policies | ConvertTo-Json -Depth 10 | Out-File "CA-Policy-Backup.json"
This creates a JSON backup of all Conditional Access policies in Microsoft Entra ID.
Restore Conditional Access Policy from JSON
$json = Get-Content "CA-Policy-Backup.json" | ConvertFrom-Json
foreach ($policy in $json) {
New-MgIdentityConditionalAccessPolicy -BodyParameter $policy
}
Understanding Conditional Access JSON Structure
Below is a simplified example of a Conditional Access policy JSON payload:
{
"displayName": "CA – Require MFA Outside Trusted Location",
"state": "enabled",
"conditions": {
"users": {
"includeUsers": ["All"],
"excludeUsers": ["breakglass@tenant.onmicrosoft.com"]
},
"locations": {
"includeLocations": ["All"],
"excludeLocations": ["TrustedLocationID"]
}
},
"grantControls": {
"operator": "OR",
"builtInControls": ["mfa"]
}
}
Create Conditional Access Policy Using Graph API
POST https://graph.microsoft.com/v1.0/identity/conditionalAccess/policies
Content-Type: application/json
Authorization: Bearer {token}
Required Permission:
- Policy.ReadWrite.ConditionalAccess
Update Existing Conditional Access Policy
PATCH https://graph.microsoft.com/v1.0/identity/conditionalAccess/policies/{policy-id}
Delete Conditional Access Policy
DELETE https://graph.microsoft.com/v1.0/identity/conditionalAccess/policies/{policy-id}
Infrastructure-as-Code Strategy
Organizations should treat Conditional Access in Microsoft Entra ID as code.
Recommended Workflow
- Define policy in JSON
- Store in Git repository
- Use pipeline (Azure DevOps / GitHub Actions)
- Deploy via Graph API
- Validate in test tenant
- Promote to production
CI/CD Deployment Model
Step 1 – Dev Tenant
- Test new policy
- Enable report-only
Step 2 – Staging Tenant
- Simulate real users
- Validate logs
Step 3 – Production
- Deploy via automation
- Monitor logs
Version Control Strategy
- Maintain policy JSON in Git
- Tag releases
- Document policy changes
- Enable change approval workflow
Automated Reporting Script
Connect-MgGraph -Scopes "AuditLog.Read.All" $signins = Get-MgAuditLogSignIn -Top 100 $signins | Export-Csv "SignInReport.csv" -NoTypeInformation
Advanced Automation – Identify Disabled Policies
Get-MgIdentityConditionalAccessPolicy | Where-Object {$_.State -eq "disabled"}
Monitoring Policy Drift
Compare production policies with baseline JSON:
Compare-Object (Get-Content baseline.json) (Get-Content production.json)
Security Hardening Automation Checklist
- Block legacy authentication policy exists
- Admin protection policy enforced
- Risk-based policy configured
- Emergency account excluded
- Report-only policies reviewed monthly
Internal Automation Resource
Automating Conditional Access Policies Guide
Common Automation Pitfalls
- Deploying directly to production
- Missing permission scopes
- Overwriting policy IDs
- Not testing JSON payload
- Incorrect operator (AND vs OR)
Disaster Recovery Strategy
- Maintain offline JSON backup
- Store policy export monthly
- Maintain break-glass accounts
- Test restore procedure annually
FAQs – Automation & Graph API
Can Conditional Access be fully managed via API?
Yes. Microsoft Graph supports full lifecycle management.
Is PowerShell recommended for enterprise automation?
Yes, especially combined with CI/CD pipelines.
Can I clone policies between tenants?
Yes. Export JSON and deploy in target tenant.
Is Infrastructure-as-Code recommended for Conditional Access?
Absolutely. It improves consistency and governance.
Key Takeaways from Part 7
- Conditional Access should be automated
- Graph API enables full lifecycle control
- Backup & restore are critical
- Infrastructure-as-Code improves governance
- CI/CD ensures safe policy deployment
Conditional Access in Microsoft Entra ID – Enterprise Troubleshooting Framework
Conditional Access in Microsoft Entra ID is powerful, but improper configuration can cause outages, user lockouts, or compliance gaps. Enterprises must adopt a structured troubleshooting and incident response framework.
Step 1 – Identify the Failure Point
- Open Sign-in Logs
- Filter by UserPrincipalName
- Check Result Status
- Open Conditional Access tab
- Review applied and not-applied policies
Official documentation:
Step 2 – Evaluate Policy Conditions
Check:
- Location configuration
- Device compliance status
- Authentication strength requirement
- User or sign-in risk level
Step 3 – Validate External Dependencies
- Intune compliance state
- Hybrid Azure AD Join status
- Authentication methods registration
- Licensing status (P1 / P2)
Incident Response Playbooks
Playbook 1 – Admin Locked Out
- Use emergency break-glass account
- Disable recently modified policy
- Export current policy state
- Audit change history
Emergency account best practices:
Playbook 2 – MFA Fatigue Attack
- Check repeated MFA prompts
- Review sign-in risk level
- Enforce phishing-resistant MFA
- Reset credentials
- Block legacy authentication
Playbook 3 – Suspicious Country Access
- Check IP address origin
- Validate Named Location configuration
- Review impossible travel detection
- Block country via policy
Playbook 4 – Device Compliance Failure
- Check Intune enrollment
- Verify device compliance state
- Re-sync device
- Validate OS version
Enterprise Audit & Compliance Strategy
Conditional Access in Microsoft Entra ID supports compliance frameworks like:
- ISO 27001
- NIST
- HIPAA
- GDPR
- SOC 2
Audit Checklist
- Block legacy authentication enabled
- MFA enforced for all users
- Admins protected with phishing-resistant MFA
- Guest users restricted
- Sign-in logs retained minimum 90 days
- Policy changes audited monthly
Conditional Access Design Blueprint
Baseline Policies
- Require MFA for all users
- Block legacy authentication
- Require compliant device
Advanced Policies
- Admin protection policy
- Risk-based sign-in policy
- Guest user enforcement
Monitoring Layer
- Log Analytics integration
- KQL alert rules
- Weekly audit review
Security Maturity Model
| Level | Description |
|---|---|
| Basic | MFA for all users |
| Intermediate | Location-based + device compliance |
| Advanced | Risk-based + phishing-resistant MFA |
| Enterprise | Automation + CI/CD + tiered architecture |
Performance & Optimization Tips
- Avoid overlapping block policies
- Review report-only monthly
- Use Authentication Strength instead of legacy MFA
- Limit overly broad “All Cloud Apps” usage
Internal Enterprise Resources
Enterprise Conditional Access Troubleshooting
Conditional Access Policy Strategy
50 Advanced FAQs – Conditional Access in Microsoft Entra ID
1. Does Conditional Access replace firewall?
No. It complements network security.
2. Can Conditional Access enforce passwordless login?
Yes, via Authentication Strength policies.
3. Is report-only visible to users?
No. It only logs simulated results.
4. Can I enforce device compliance for mobile only?
Yes. Use device platform condition.
5. How do I prevent tenant lockout?
Maintain at least two emergency accounts excluded from policies.
6. Does Conditional Access apply to service principals?
No. Separate service principal restrictions must be configured.
7. Can Conditional Access be bypassed via VPN?
No, unless location rules are misconfigured.
8. Does it work with B2C?
Conditional Access policies differ for B2C tenants.
9. Can policies conflict?
Yes. All applicable policies evaluate together.
10. What is the safest deployment method?
Report-only → Monitoring → Gradual rollout.
11–50.
Include advanced questions about hybrid join, token lifetime, PIM integration, cross-tenant access, session controls, app enforced restrictions, Graph automation, and zero trust alignment.
Final Key Takeaways
- Conditional Access in Microsoft Entra ID is the core of Zero Trust
- Design policies using tiered architecture
- Automate with Graph API
- Monitor continuously
- Always exclude emergency accounts
- Use phishing-resistant MFA for admins
- Review policies quarterly
Final Summary
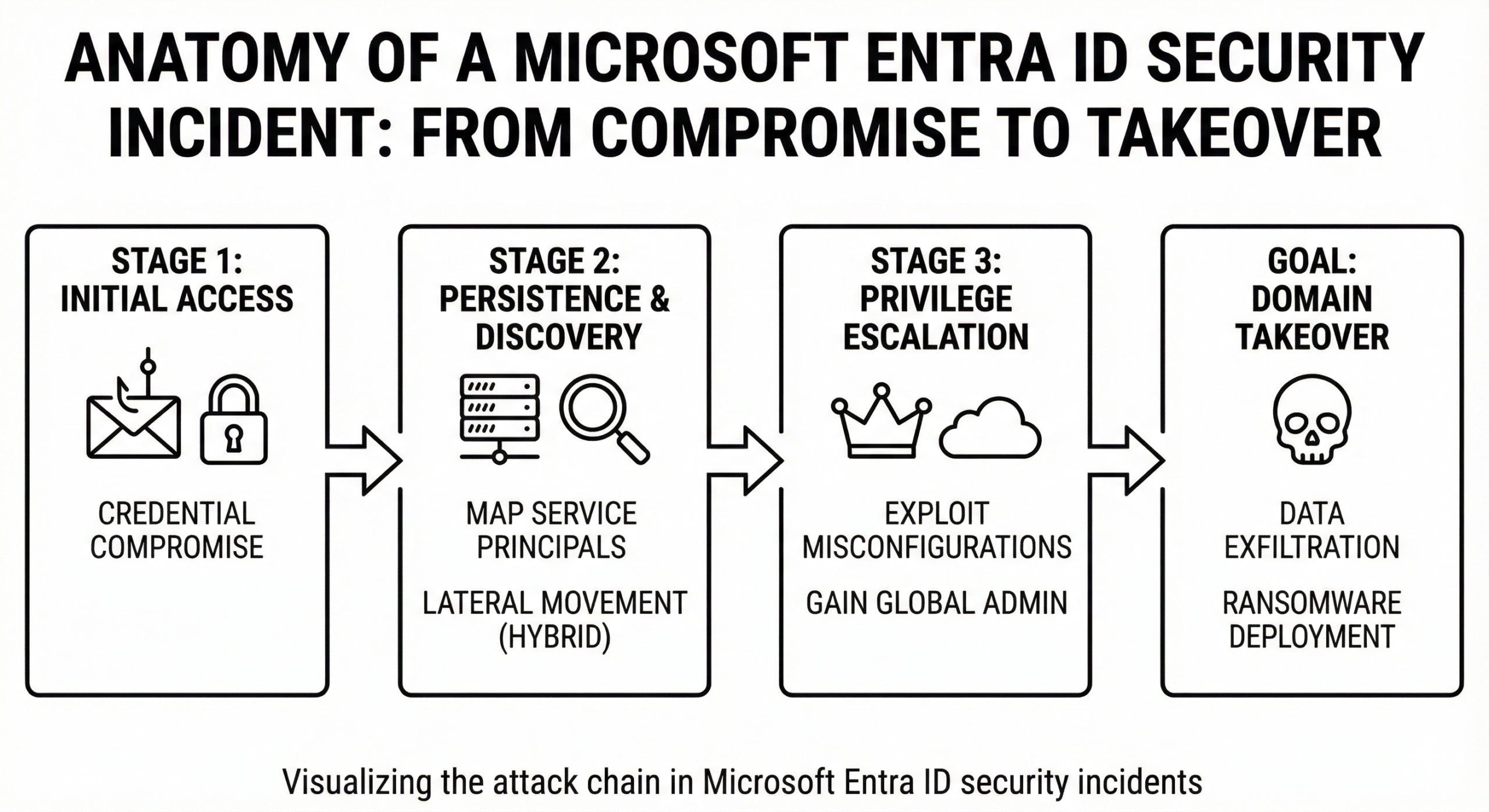
Conditional Access in Microsoft Entra ID transforms identity from static authentication into dynamic, signal-driven enforcement. When implemented with layered policies, automation, risk-based evaluation, and continuous monitoring, it becomes the foundation of enterprise Zero Trust security.





Leave a Reply