1. Introduction to Microsoft Entra External ID
Microsoft Entra External ID is the next evolution in Customer Identity and Access Management (CIAM), designed to replace and expand upon Azure AD B2C while integrating B2B collaboration under a unified platform.
Why CIAM Matters
Consumer-Facing Apps: Retail, healthcare, banking, and SaaS need secure, scalable identity solutions.
B2B Collaboration: Secure partner access without compromising governance.
Regulatory Compliance: GDPR, NIS2, and other frameworks require robust identity security.
Microsoft Entra External ID is built for security-first, developer-friendly, and fully customizable experiences.

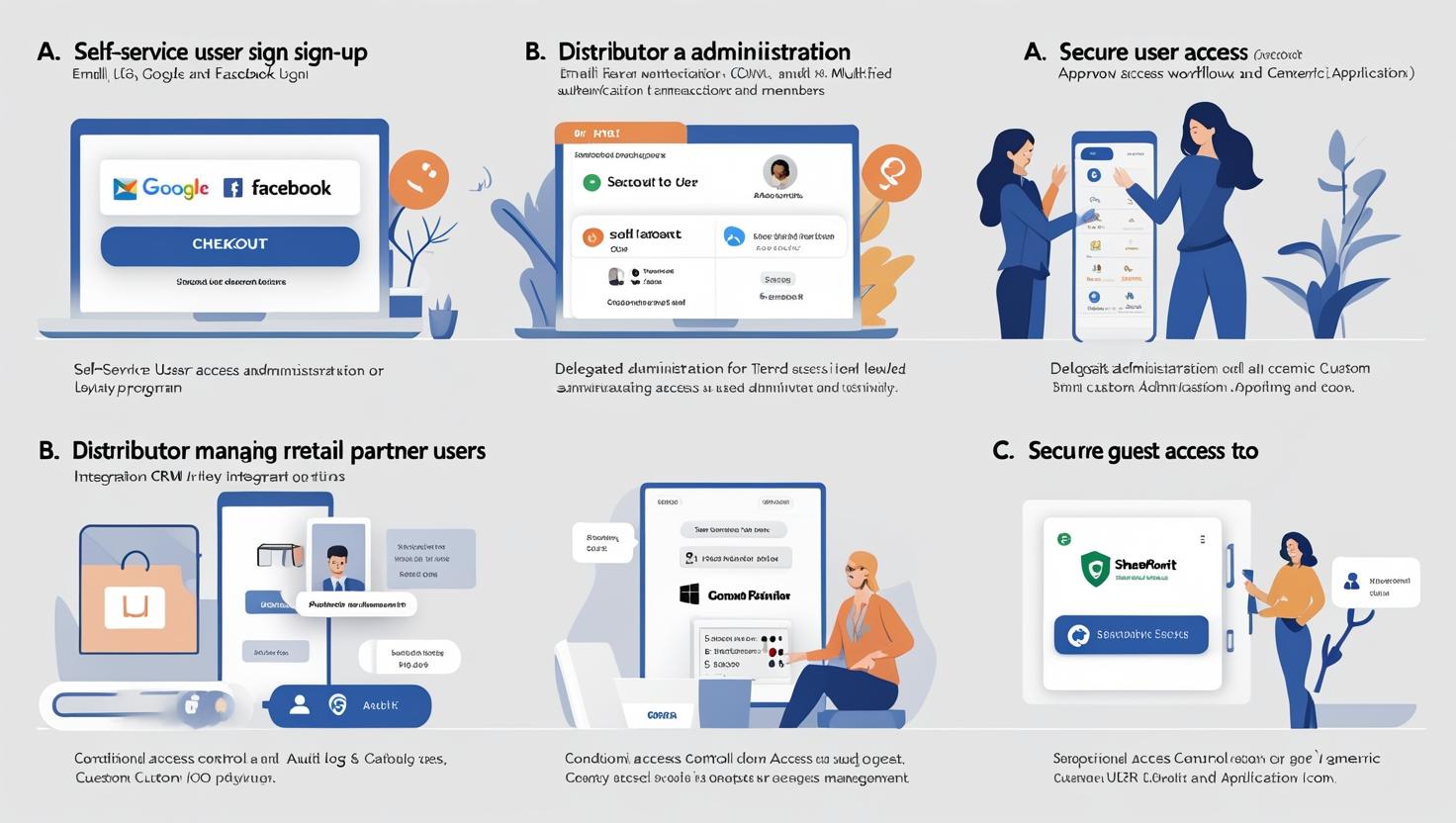
2. Core Scenarios & Use Cases
A. Consumer Identity (B2C)
Self-Service Sign-Up: Users register via email, social logins (Google, Facebook), or phone.
Checkout Flows: Step-up authentication for high-value transactions (e.g., MFA on purchases >$50).
Personalization: Dynamic UI based on user segments (e.g., loyalty program members).
B. Business Customer Identity (B2B2C)
Delegated Administration: Let distributors manage their users (e.g., a supplier managing retail partners).
Custom Auth Policies: Approvals, tiered access, and CRM integrations.
C. Business Collaboration (B2B)
Secure Guest Access: Partners access SharePoint, Dynamics 365, or custom apps.
Governance: Conditional Access, audit logs, and lifecycle management.
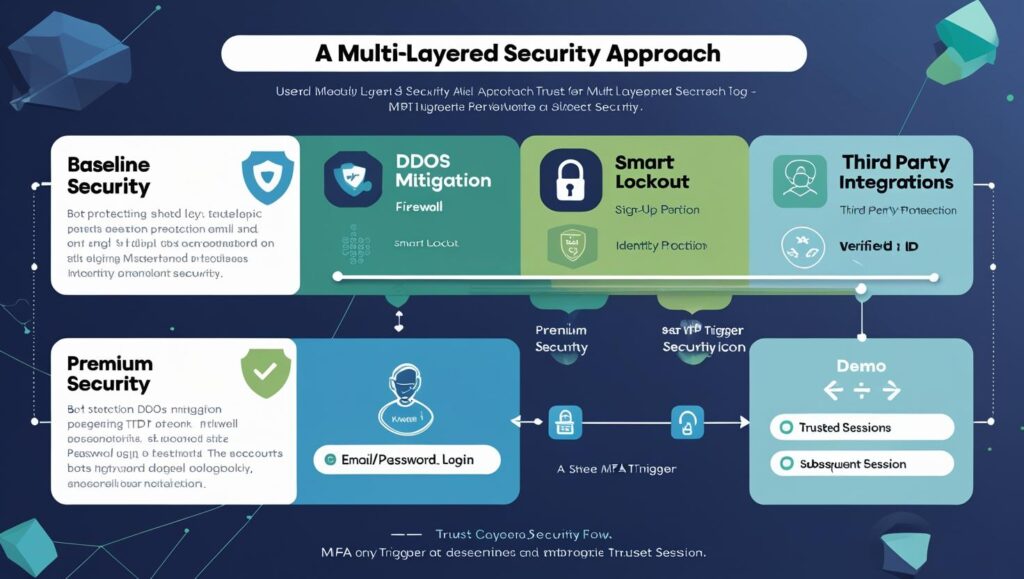
3. Security: A Multi-Layered Approach
A. Baseline Security (Included by Default)
| Feature | Description |
|---|---|
| Bot Protection | IP throttling, CAPTCHA, and rate limiting. |
| DDoS Mitigation | Blocks Layer 3/4 attacks (SYN floods, UDP reflection). |
| Smart Lockout | Stops brute force attacks without locking legitimate users. |
| HTTP Attack Prevention | Protects against Slowloris, Rapid Reset, and other exploits. |
B. Premium Security (Add-Ons)
| Feature | Use Case |
|---|---|
| Sign-Up Fraud Protection | Detects fake emails, disposable domains. |
| Identity Protection | Risk-based Conditional Access (e.g., block logins from Tor networks). |
| Third-Party Integrations | Fraud detection (e.g., Arkose Labs, Microsoft Defender for Identity). |
| Verified ID | Decentralized identity for KYC/compliance. |
Demo: Step-Up Authentication
User signs in with email + password.
At checkout (>$50), MFA is triggered (SMS/email OTP).
Subsequent high-risk actions skip MFA (session remains trusted).
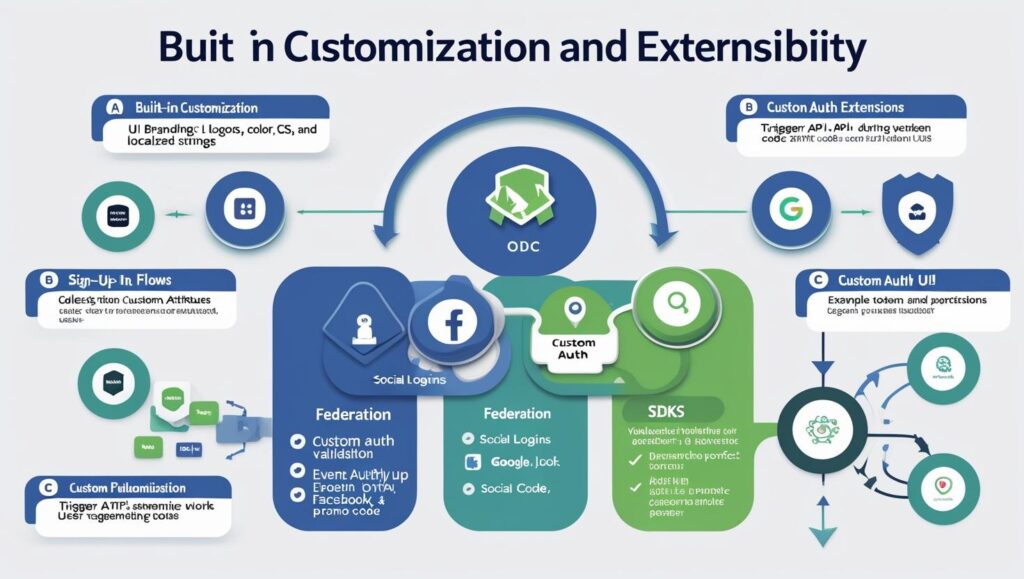
4. Customization & Extensibility
A. Built-In Customization
UI Branding: Logos, colors, CSS, and localized strings.
Sign-Up Flows: Collect custom attributes (e.g., loyalty ID, promo code).
Federation: Social (Google, Facebook), SAML, OIDC.
B. Custom Auth Extensions (Replaces Azure AD B2C API Connectors)
Event-Based Hooks: Trigger APIs during:
Token Issuance (add custom claims).
Attribute Collection (pre-fill data from CRM).
User Validation (block disposable emails).
Example: Dynamic Promo Code Validation
User enters promo code at sign-up.
Custom Auth Extension calls an API to validate.
If valid, user gets gold-tier access; else, error appears.
C. SDKs for Pixel-Perfect UIs
Native Mobile (iOS/Android)
SPA (React, Angular)
Backend (Node.js, .NET)
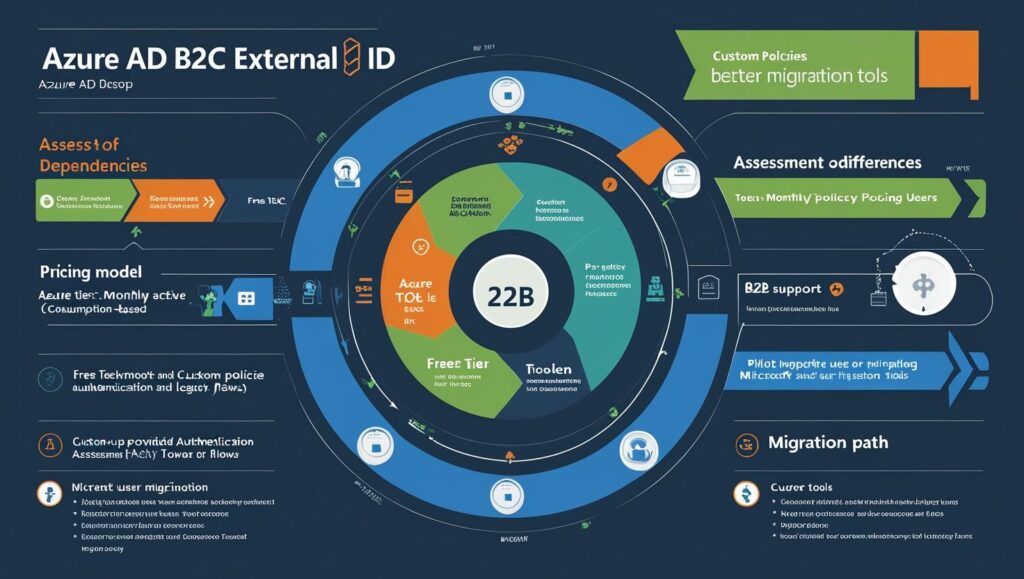
5. Migration from Azure AD B2C
Key Differences
| Feature | Azure AD B2C | Entra External ID |
|---|---|---|
| Custom Policies | XML-based, complex | Replaced by Custom Auth Extensions |
| Pricing | Per-auth + MAU | Free 50K MAUs, then consumption-based |
| B2B Support | Limited | Unified with B2C/B2B2C |
Migration Path
Assess Dependencies
Are you using custom policies? Plan for SDKs + Extensions.
Does your app rely on legacy B2C features? Check parity.
Pilot Testing
Test sign-up, auth, and token flows.
Cutover
Microsoft will provide tools for user migration.
6. Pricing & ROI
Cost Breakdown
| Tier | Price |
|---|---|
| First 50K MAUs | Free |
| 50K+ MAUs | $0.03/MAU ($0.016 promo first year) |
| Identity Governance Add-On | $0.75/MAU |
Why It’s Cost-Effective
No per-auth fees (unlike Auth0, Okta).
Azure Integration: Monitor logs in Sentinel, reducing SIEM costs.
7. Roadmap & Future Enhancements
Coming Soon
Username Logins (non-email, e.g., loyalty numbers)
Terraform Support (IaC deployment)
More Custom Auth Extension Hooks
SAML/OIDC Federation Improvements
8. Final Recommendations
Who Should Adopt Entra External ID?
✔ New CIAM projects (start here instead of Azure AD B2C).
✔ Azure AD B2C users (plan migration before 2025).
✔ Enterprises needing B2B + B2C in one platform.











Leave a Reply